Yesterday at the end of the day, I was called by our PR team who got alerted by tech support about a Twitter post that was going viral. Turns out a custom phishing test created by one of our customers had backfired. KnowBe4 has 35,000 customers as I write this, and we send more than 10 million simulated phishing tests a month. So, you can expect now and then something goes wrong. It rarely happens, but when it does it can get a lot of airplay.
Erik Wemple at the Opinion section of the Washington Post reported that "There are few places in contemporary media where the dangling of a phony bonus would receive a worse reception than at Tribune Publishing. Employees of the newspaper colossus — which owns the Chicago Tribune, the Orlando Sentinel, the New York Daily News, the Capital Gazette and the Maryland Gazette — have been subjected to furloughs, pay cuts and, in several cases, the closure of their shared workspaces."
He continued: " All of which provides context for the email that Tribune Publishing employees received on Wednesday. “Congradulations Executives!!” started the email — and yes, the typo is in the original. It explained that the company is “pleased to inform you that we are providing targeted bonuses between 5,000 and 10,000 dollars this year. Tribune Publishing is able to provide this bonus as a direct result of the success created by the ongoing efforts to cut our costs!” The email then instructs employees to “login” to “view your end of year bonuses.”
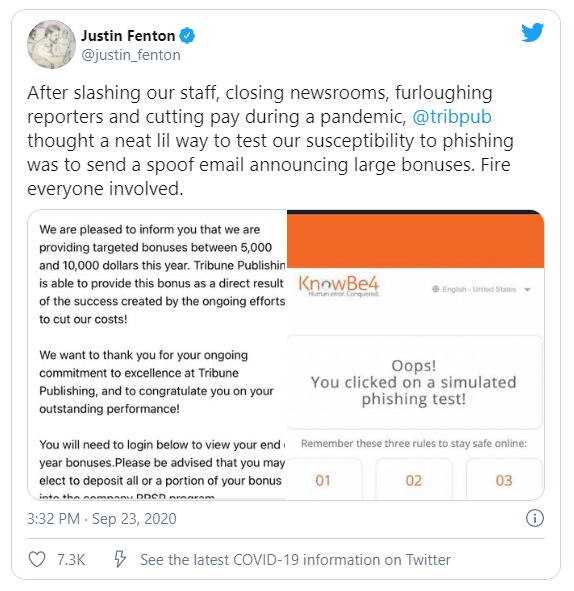 On Twitter, the comments were that the test came across as disrespectful, a slap in the face and tone-deaf. That reaction is understandable. Simulated phishing tests need to be sensitive to the existing corporate culture and circumstances.
On Twitter, the comments were that the test came across as disrespectful, a slap in the face and tone-deaf. That reaction is understandable. Simulated phishing tests need to be sensitive to the existing corporate culture and circumstances.
However, that is sometimes a fine line to walk, because the bad guys don't care about those values at all, and will use any distasteful social engineering tactic to get an employee to click so that they can take over the workstation and shut the whole company down with ransomware. KnowBe4 sees malicious spear-phishing attacks like this every day, reported by employees through their Phish Alert Button. However, simulated phishing campaigns do need to be sensitive to the current scene, and Tribune apologized to their employees:
"Today the company conducted a regular, internal test to assess and reduce its current phishing and malware risk level. Based on input provided by the company’s cybersecurity team and advisers, the content of that test included language regarding employee bonuses. Having fallen victim to attacks of this nature before, the company recognized that bad actors use this type of language regularly, and decided to use the language to simulate common phishing scams.
The company had no intention of offending any of its employees. In retrospect, the topic of the email was misleading and insensitive, and the company apologizes for its use."
You see how this can be a difficult position to be in. Employees click on attacks like this but you do need to build a strong human firewall. KnowBe4 has 5,000 templates that are known to work, clearly sorted in categories—one of them called "controversial"— and each template is rated with a 5-star system regarding difficulty.
We even have an automated campaign where we take real phishing attacks that came in from the bad guys, "defang" them, and provide those as templates. If there is any doubt, we recommend running a small pilot of the campaign and test it before sending it to the full employee list.
There are effective, known to work ways to create a strong human firewall and enable employees to make smarter security decisions every day. The human still is the weak link in IT security and used right, the KnowBe4 platform is a great way to manage the ongoing problem of social engineering.




