 One of the challenges with living in a hyper-connected world is that it’s easy for anyone to stand on a soapbox and point out when something is wrong.
One of the challenges with living in a hyper-connected world is that it’s easy for anyone to stand on a soapbox and point out when something is wrong.
Gone are the days where people would largely keep their opinions and views to themselves or limited to their social circle.
Cybersecurity is not immune to this phenomenon. Every breach, hack, misconfiguration, and incident are examined, picked apart, and criticised on the most public of forums.
This, in many ways impacts the esteem of many organisations. Not too dissimilar to how perfect bodies in movies and Instagram have led people to undertake more and more cosmetic surgery. According to the International Society of Aesthetic Plastic Surgery (ISAPS), there are around eight surgeries a minute in the U.S. alone. Other countries where plastic surgery is popular include Brazil, Mexico, Germany, and India.
People will often pursue an image of perfection that will supposedly make them content. The removal of a bump on the nose, a little bit of filler in the lips, removal of some fat…the list goes on and on.
This is pretty much what we see mirrored in cybersecurity. We start at a similar point, fixating on the flaws, so when an organization gets breached, we immediately jump to fixing those flaws, “If only they had implemented 2FA”, “if only they had a SIEM”, “Why didn’t they have anti-DDoS protection”, “Next generation endpoint protection would have saved them.”
In the pursuit of cyber perfection, we see most organisations rush to implement a technology in the belief that it will solve all issues quickly.
This isn’t a new phenomenon either. In 2013, Wendy Nather wrote a paper entitled, “The Real Cost of Security.” In this paper, Wendy asked security leaders what security technologies they would buy for a 2,000-person company.
The resulting list that came back resembled the controls recommended by PCI DSS. Why was that? Well, one of the reasons is that those kinds of technology-focussed lists are what we’ve been conditioned to expect. Security leaders believe that unless they go and invest in all sorts of bells and whistles, they will be left behind.
Our attempts as an industry at fulfilling our security needs through total security technology is completely backwards.
Dr. Brené Brown is a research professor at the University of Houston Graduate College of Social Work. She has spent the past 13 years studying vulnerability, courage, worthiness, and shame.
She says about perfection:
“…a self-destructive and addictive belief system that fuels this primary thought: If I look perfect and do everything perfectly, I can avoid or minimize the painful feelings of shame, judgment, and blame.”
Let’s change that to this:
“…a self-destructive and addictive belief system that fuels this primary thought: If I do perfect security, buy the perfect security tools, and hire the best security professionals, I can avoid or minimize the painful feelings of shame, judgment, and blame.”
Upon reflection, much like perfection, the question becomes, “When are we done?” Or, to put it in other words, “What does the perfect level of security look like?”
Is it when we have firewalls everywhere? Or is it when your security operations centre resembles NASA’s mission control?
The Paradox of Choice
The paradox of choice is when someone becomes overwhelmed with too many options.
For example, when you go to a large conference and see hundreds of vendors, does it make you feel more confident in your buying abilities or more confused.
There’s an example of a shoe seller who out-sold all his competitors. His secret was this…A customer would come in and ask to see a pair of shoes, then another. But when they asked to see a third pair, he would ask which one to take away, so the customer only ever had two options in front of them and thus the decision to buy was a lot easier.
When we look for too many answers, or when we fixate on too many problems, we will inevitably spend too long chasing our tails. Very often, the tools and resources we need are already in front of us, and a lot more simple than we think.
Persistence and Acceptance
The trick to improving security is to persist; or to be consistent while accepting limitations.
For example, when trying to get fit, it can be easy to be distracted by fancy exercise equipment, supplements, diet plans or even liposuction. But ask yourself this, if someone walked every day and cut out some unhealthy snacks from their diet, would their overall health and fitness improve or not at the end of the year? In the majority, if not all cases, you will agree that the person will end up being healthier.
This is one of the underlying principles of new-school security awareness training. You don’t look for a quick fix or a fancy technology. Rather, you persist with simulated phishing and user training over a long period of time to improve security.
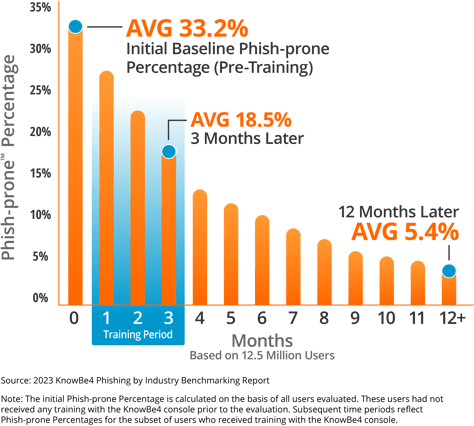
That’s a statement backed up by actual data, as showcased in the KnowBe4 2021 Phishing by Industry Benchmark Report. The results clearly show when organisations start, an average Phish-Prone™ percentage, which indicates how many of their employees are likely to fall for a phishing or social engineering scam, of 31.4%. The data showed that this can be brought down by over half to 16.4% in only 90 days by deploying new-school security awareness training. The one year-plus results show that with continuous testing and training, the final average drops to around 4.8%
So, the question remains, are you going to spend time chasing security perfection? Or adopt a proven and simple way to reduce one of the largest threats to your organization?



 New-school Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn't a one and done deal, continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your one-on-one demo of KnowBe4's security awareness training and simulated phishing platform and see how easy it can be!
New-school Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn't a one and done deal, continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your one-on-one demo of KnowBe4's security awareness training and simulated phishing platform and see how easy it can be!













