 Cisco's Talos Labs researchers had a look into the future and described how ransomware would evolve. It's a nightmare. They created a sophisticated framework for next-gen ransomware that will scare the pants off you. Luckily they also came up with suggestions for how to design a ransomware-resistant architecture. Their report is called: "Ransomware: Past, Present, and Future".
Cisco's Talos Labs researchers had a look into the future and described how ransomware would evolve. It's a nightmare. They created a sophisticated framework for next-gen ransomware that will scare the pants off you. Luckily they also came up with suggestions for how to design a ransomware-resistant architecture. Their report is called: "Ransomware: Past, Present, and Future".
In this (quite long) blog post they give you the history of ransomware and they provide some recent examples including the emergence of Locky and the February attack against Hollywood Presbyterian Medical Center.
Here is what they said when they looked in their Crystal Ball:
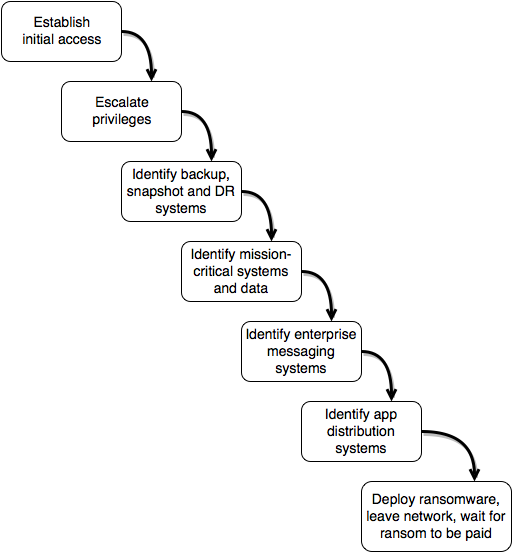
"The attackers have domain admin access, and have mapped the network as required. Access to backup systems, mission critical systems, messaging servers, and application distribution platforms has been acquired. The attackers pulled hashes from NTDS.dit and through a combination of coming across tools/scripts using hardcoded credentials and other means, came across a few passwords for other valuable domain accounts. Using that as a template along with the rockyou password cracking wordlist, a number of passwords have been cracked. The attackers have determined that it is time to strike and use the ransomware framework to generate a ransomware payload with the following settings:
"The payload generated demands 1 million dollars USD in bitcoin to be delivered in 8 days, tripling to 3 million dollars if payment is not made in 8 days. The instructions mention a .onion address (hidden service) and provide instructions on how to use tor2web or the Tor Browser Bundle, and how to purchase bitcoins. Since the attackers know where all the important applications, drives and data are located, they have included custom directories and file extensions for the ransomware to attempt to encrypt as a part of the core implant."
The study expects this next-gen ransomware will make use of several malicious, integrated modules. The "rate limiter" module would strategically limit the ransomware's CPU usage and attempt to stay under the radar and use as little system resources as possible. The Command & Control plugin allows the crypto-malware to contact a C&C domain via a GUID, much harder to detect than the normal.
With these advanced modules, the cybercriminals make sure that if defense systems pick up on them, they can change tactics. Adaptability like that allows them to move laterally throughout an infected network and identify all of the key business assets that might stand in their way, such as backup drives, messaging servers, and systems responsible for performing software application pushes.
The study predicts that taking out those resources would leave the target organization very vulnerable:
"Once launched, the malware is more or less unstoppable. In the span of an hour, over 800 servers and 3200 workstations are compromised; half the organization's digital assets, and the vast majority of the company's data are encrypted. Disaster Recovery mode is initiated, but the DR environment was also compromised due to shared credentials and poor segmentation. The target is forced back into the 1980s: digital typewriters, notebooks, fax machines, post-it notes, paper checks and the like. The victim is left with a choice: Do we pay the ransom, set a precedent and rapidly recover? Or do we refuse to pay the ransom and potentially make the recovery much longer and more difficult with a guaranteed loss of data?"
The study has a name for this mishmash of threats: "cryptoworms."
This nightmare scenario that the study envisions is a blueprint for cybercriminals that are I'm sure salivating just thinking about having this kind of attack platform. The picture they paint is a type of ransomware that has rapid propagation, fast payload delivery, with ability to cripple recovery efforts similar to an actual computer worm. The study has a name for this mishmash of threats: "cryptoworms," and suggests you should focus on enhancingyour organization's defense in depth through DMZ hardening, secure backups and employee security awareness training.
Looking at the above, it is imperative that any organization makes sure they become a hard target as soon as possible.
Computer criminals go where the low-hanging fruit is. They social engineer an employee to enter their credentials and they are in your network. An organization's first line of defense is its employees. You need to create a human firewall. The harder you are as a target, the less chance of a ransomware infection.
Get a demo and see how easy it is to train and phish your end-users.





