A modified version of EDA2, an open source ransomware strain developed by Turkish computer engineering student Utku Sen, --by the way, thanks Utku, that was a very smart idea-- has been encrypting files and appending the .surprise extension to them. The cybercriminals using the Surprise ransomware have chosen an unusual infection vector: the popular remote control tool TeamViewer.
The first time this was mentioned was in a forum post on Bleeping Computer on March 9th, and as more machines got infected, victims were able to upload the malware executable to the forum for analysis. When the string was pulled, it turned out that all of them were using TeamViewer v10.0.47484.
“Moreover, the analysis of TeamViewer traffic logs showed that someone had remotely executed the surprise.exe process on computers, which resulted in malware injection behind the scenes,” noted PrivacyPC’s David Balaban. He also reported on a new criminal approach: negotiated ransom.
"The files can only be recovered if the victim pays a ransom in Bitcoins. Interestingly enough, the amount depends on how important the locked data is, and it may range from 0.5 BTC to as much as 25 BTC. These terms are to be negotiated individually. Obviously, if this ransom Trojan hits an enterprise network consisting of multiple machines, the ransom will be much higher than in a single PC assault scenario. The cybercriminals are also “kind” enough to decrypt one file for free, which is sort of a cold comfort to the target. This way, the black hats simply try to prove they are actually able to restore the frozen data."
Another wrinkle is that more than one user ID was used to infect systems, and that in some cases the box had been owned for months. Here is an example of a TeamViewer log:
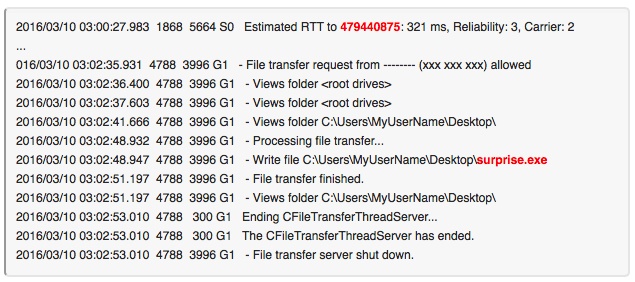
People were suggesting this could be caused by a TeamViewer data breach but that does not necessarily follow. TeamViewer PR Manager Axel Schmidt denied it: “We looked thoroughly at the cases that were reported to us. According to our investigation, the underlying security issues cannot be attributed to TeamViewer. Thus far we have no evidence that would suggest any potential security breach of TeamViewer that attackers exploit.
"Furthermore, a man-in-the-middle attack can nearly be excluded because of TeamViewer’s deployed end-to-end encryption,” he wrote in a public statement. "Additionally, we have no reason to believe that a brute-force attack is the origin of the reported infections. TeamViewer exponentially increases the latency between connection attempts. It thus takes as many as 17 hours for 24 attempts."
Sounds like they have reasonable security measures in place. So what can cause this?
Well, TeamViewer brings up a good point: carelessness of users who use the same password across multiple accounts with various suppliers. If a hacker gets one password and it's the same for multiple accounts, they can do a lot more damage.
Alex Schmidt continued: “As TeamViewer is a widely spread software, many online criminals attempt to log on with the data of compromised accounts, in order to find out whether there is a corresponding TeamViewer account with the same credentials. If this is the case, chances are they can access all assigned devices, in order to install malware or ransomware.”
They came up with some very good advice, something we have advocated here for years: use unique and strong passwords for all your user accounts before you're infected. They also recommended to protect TeamViewer accounts using their two-factor authentication, which is something you should do for all your critical logins like email, banking and sites that contain personal, confidential information like your healthcare data. I'd recommend to check with these types of sites if they provide two-factor authentication and if they do not, use another provider that does.
Here is something else you can do about ransomware now.
Get the most informative and complete hostage rescue manual on Ransomware. This 20-page manual (PDF) is packed with actionable info that you need to prevent infections, and what to do when you are hit with malware like this. You also get a Ransomware Attack Response Checklist and Prevention Checklist.
Related Pages: Ransomware





