 Once again, the human layer continues to be the most desirable attack vector for cybercriminals. 2022 marks the 5th year KnowBe4 has analyzed hundreds of millions of elements of data in order to provide the 2022 Phishing by Industry Benchmark Report.
Once again, the human layer continues to be the most desirable attack vector for cybercriminals. 2022 marks the 5th year KnowBe4 has analyzed hundreds of millions of elements of data in order to provide the 2022 Phishing by Industry Benchmark Report.
The report analyzes Phish-prone™ Percentage (PPP) across millions of individual users pulled from anonymized KnowBe4 customer data. The report illustrates how crucial it is for organizations to invest in their employees to increase their overall defense capabilities. Think of it this way, if you do not give your employees the right tools to be better equipped at identifying attacks, you could be leaving your organization open to vulnerabilities that could cause major operating, financial and brand disruption.
So, if you know humans are this important…what are you waiting for?
If you aren’t familiar with our Phishing by Industry Benchmarking Report, let me catch you up. The purpose of this report is to analyze and understand the impact of a new-school security awareness approach on an organization’s susceptibility to phishing or social engineering attacks. To do this, we analyze data from three phases:
- Phase One: If you haven’t trained your users and you send a phishing attack, what is the initial resulting PPP? To do this, we monitored employee susceptibility to an initial baseline simulated phishing security test. From that established set of users, we look at any time a user has failed a simulated phishing security test prior to having completed any training.
- Phase Two: What is the resulting PPP after users complete training and receive simulated phishing security tests within 90 days after training? We answered this question by finding when users completed their first training event and looking for all simulated phishing security events up to 90 days after that training was completed.
- Phase Three: What is the final resulting PPP after users take ongoing training and monthly simulated phishing tests? To answer this, we measured security awareness skills after 12 months or more of ongoing training and simulated phishing security tests, looked for users who completed training at least one year ago, and took the performance results on their very last phishing test.
This year’s inclusion dataset spanned 19 industries and comprised over 9.5 million users across 30,173 organizations with over 23.4 million simulated phishing security tests. In addition to North America, we expanded our analysis of global data in order to provide insights in the following regions: Africa, Asia-Pacific, Europe, South America and the United Kingdom/Ireland.
The Phishing by Industry Benchmarking Report is great for helping you evaluate your organization’s Phish-prone Percentage (the “what?”) and to find context (the “so what?”). It gives you that extra bit of contextual data you need to know so you can gain an accurate understanding of how your organization compares to others. That’s immensely valuable because it helps push you to that final “now what?” question… and that’s where things get really interesting.
Here’s what we found:
For 2022, the overall PPP baseline average across all industries and size organizations was 32.4%, meaning just less than a third of an average company’s employee base could be at risk of clicking on a phishing email.
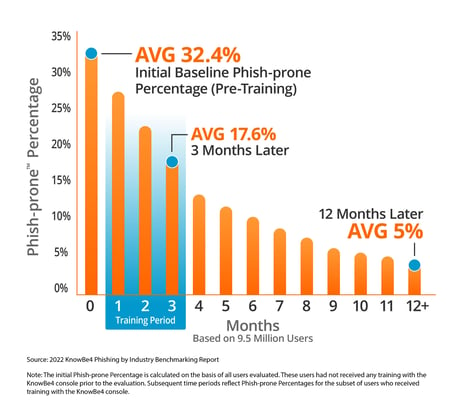
However, only 17.6% of those same users will fail within 90 days of completing their first KnowBe4 training. After at least a year on the KnowBe4 platform, only 5% of those users will fail a phishing test. Organizations improved their susceptibility to phishing attacks by an average of 85% in one year by following our recommended approach.
Why this is important:
Among the thousands of clients I engaged with during my time leading the security awareness and training space at Gartner, there was one thing that consistently astounded me: how little most organizations were doing to improve the readiness of their human defense layer.
Most organizations view training as something they have to do (checking the box) rather than something that will help drive a more secure culture in which every employee understands the importance, and responsibility, of being more security-aware in their professional and personal lives.
You can’t turn focus on the human element on and off like a light switch. Only a comprehensive and ongoing program (yep, there is no end), will change behaviors; breaking old bad habits and developing new and more secure ones.
A few things to keep in mind…
- It’s essential to foster a security culture. Security culture, as defined by KnowBe4,
is the ideas, customs and social behaviors of an organization that influence their security. All employees should understand what their role and responsibility is to protect the organization and themselves from being vulnerable to a cyberattack. - Increase the frequency of your security awareness training while decreasing the time invested. A regular, consistent cadence is required in order to drive substantial and sustainable behavior change.
- Work with experts. Security awareness content is like no other and should be designed by experts who understand the behavior changes required to create an effective human defense layer, while also providing an engaging learning experience. Don’t get caught in a cycle of boring, ineffective, unappealing content.
After all, KnowBe4 is not the market leader in this space by chance. We are the market leader because we have the data and have conducted the research to demonstrate the importance of the human layer. We also have the only tried-and-true program to help your organization build a more security-aware and prepared culture.
Get Access to the Report Now!
Don't like to click on redirected buttons? Cut & Paste this link in your browser: https://info.knowbe4.com/phishing-by-industry-benchmarking-report




