 Most readers will probably be familiar with the story of bank robber Willie Sutton who, after being nailed by the cops, was asked why he robbed the bank. His answer (undoubtedly delivered in the most deadpan voice one can imagine): "Because that's where the money is."
Most readers will probably be familiar with the story of bank robber Willie Sutton who, after being nailed by the cops, was asked why he robbed the bank. His answer (undoubtedly delivered in the most deadpan voice one can imagine): "Because that's where the money is."
Although criminals have gone high tech since the days of that old fashioned, pistol-packing bank robber, their motivations remain essentially unchanged. Over the past month or so we've been reminded of that very basic truth while watching the surge in phishing emails targeting payroll operations at our customers who use the free KnowBe4 Phish Alert Button (PAB). Why target payroll? Because that's where the money is.
These phishes, which are almost all examples of CEO Fraud, take several different forms.
Pay Stub Phishing
A new strain of payroll phishes that has surfaced over the past few months involves phishing emails requesting copies of pay stubs and wage statements. Both are year-round social engineering attacks that expand on the W-2 phishing campaigns which erupt at tax season. Very familiar with the ways in which this kind of confidential employee data can be exploited for fraud, some malicious actors are now turning to phishing attacks targeting the same kind of data, but now during the whole year.
We ourselves almost missed the rise of pay stub phishes, as they seemed so innocuous when we initially encountered them. Moreover, because these emails typically request a single, specific pay stub for one employee (instead of a complete collection of W-2 statements covering an organization's entire employee base), these emails seem designed to "fly under the radar" and not attract undue attention.
These malicious emails are simple, direct, and dispense with any attempt to construct believable backstories or pretexts for the request. In short, they invite an unthinking, reflexive response from targeted users.
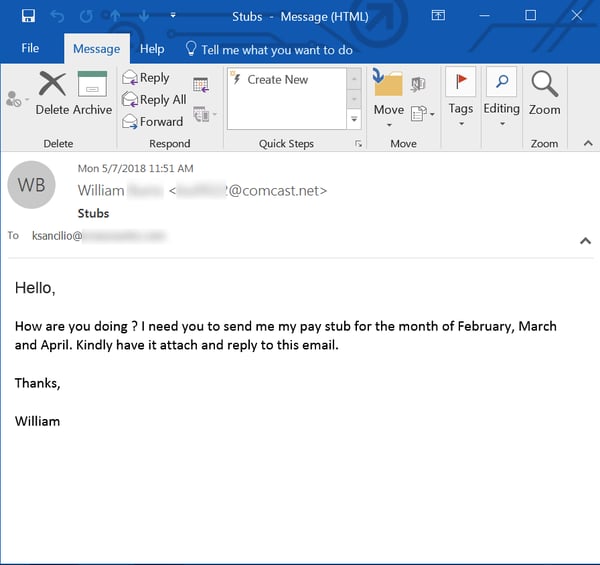
Several things eventually caught our eye. First, these phishing emails use almost identical language with small variations. Second, every single example that we've seen uses an oddball Comcast.net email address, all with nonsense usernames of similar length. We strongly suspect that this particular campaign is being run by a single group of malicious actors, and that this group is having success with the campaign, as it seems to have expanded significantly over the past 2-3 months.
Whoever this group is, the pay stub phishes we've seen tell us that these bad guys have done their research. These phishes spoof presidents, CEOs, and other C-level executives within targeted organizations. Moreover, these phishes almost unfailingly seem to land in the inboxes of employees whose work involves payroll processing.
Pay stubs typically contain much the same kinds of data that can also be found on W-2 statements, which means that they can be exploited for identity theft and other forms of financial fraud. Given that the requested pay stubs are for senior executives, the bad guys are clearly calculating that the high value of the target more than makes up for the low volume of data requested.
Although we have not seen any email exchanges between targeted employees and the malicious actors running this campaign, we do suspect that these pay stub requests could be used as a pretext to finagle help gaining access to online payroll services, which most companies are using these days.
Wage Statements
Another variation on the standard W-2 phish that we've seen is the request for "wage statements."
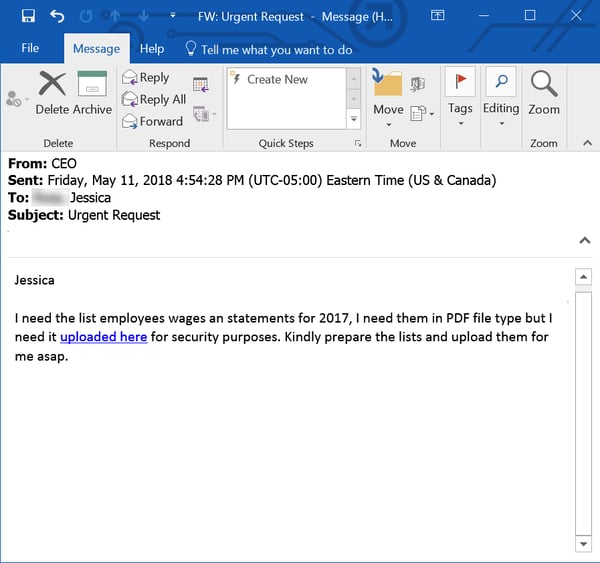
Although it is not entirely clear what specific documents are being requested here, if malicious actors, however confused they may be themselves, manage to get one of your overly solicitous employees in a back-and-forth, there's no telling what the bad guys could walk away with. Professional confidence men hot on the scent of money can be awfully persuasive.
Payroll Updates
Not content to nibble around the edges with fraudulent schemes based on purloined payroll data, some malicious actors have elected to go straight for the money with spoofed requests to change the bank accounts used to deposit the paychecks of CEOs, presidents, and other senior executives within targeted organizations.
Consider this rather simple email, which requests that employees in the payroll department of the targeted organization change the direct deposit information for a senior employee in the company:
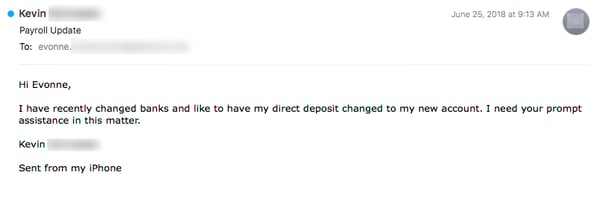
Over the past month we have seen hundreds of these phishes, all almost identically worded. Unfortunately, many of the targeted payroll employees have proven all too eager to respond to these requests, offering various forms of assistance.
Some employees respond by pointing the bad guys to online payroll services where they could presumably make the requested change themselves -- had they the login credentials to do so, of course.
Other employees helpfully request a voided check so that they can make the requested changes immediately without any further effort on the part of the bad guys.
Both of these responses have typically stymied the bad guys. These would-be fraud artists either don't have the required login credentials for the online payroll service (if they had the credentials, they already would have made the changes themselves, thank you) or they lack a cancelled check for the account they wish to start receiving direct deposits. Their usual response is to plead some form of inability to access the payroll service (a not particularly convincing excuse) or to claim that their checkbooks have mysteriously taken a walk. Both responses usually raise enough suspicion that someone hits the Phish Alert Button (PAB) and alerts IT staff.
But when C-level pay days are involved, there is always the will to find a way.
Take a look at this email exchange between Diane, a Payroll Specialist at one of our customers, and a bad guy pretending to be Steve, a senior VP at the company. The exchange starts with the usual matter-of-fact request for a change to Steve's direct deposit information.
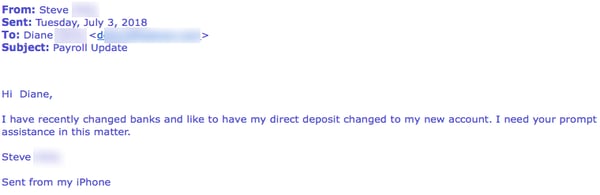
Diane responds by asking for a voided check. To everyone's surprise, the bad guy not only happily responds...
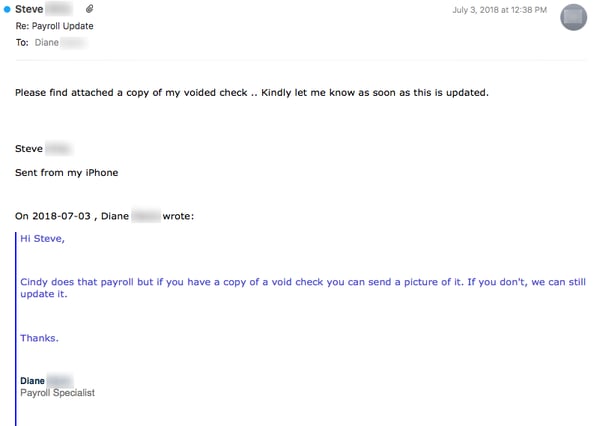
...he actually supplies one via an attached PDF:

Now, this obviously photoshopped picture of a blank check has a number of problems. First, the name on the check is visibly misaligned and lacking the usual address and phone information that most personal checks would sport. Second, the check number is 100 -- a clear indication that the bank account in question is brand spanking new. That was enough in this case for the Diane to hit the Phish Alert Button (PAB).
Although this particular payroll phish was not successful, it does demonstrate that the bad guys are more than capable of learning and adapting from previous experiences dealing with employees in these kinds of CEO Fraud operations. In this case, it appears the bad guys actually opened a bank account, ordered checks for that account, then used one of those checks to support this phishing email.
Adapt or Get Fleeced
There's a very clear lesson for employees to learn here. You can't expect all the bad guys to be completely inept all of the time. Life just isn't that easy, much to our chagrin. Yes, they do make mistakes. But they learn fast from those mistakes. They adapt. And then they come back to take another run at your organization's money and resources.
If your employees aren't learning and adapting as well, there may well come a day when some very senior muckety-mucks in your organization suddenly discover they aren't receiving paychecks any more. Or your less senior employees may wake up to find their identities have been hijacked and their tax refunds stolen. Then everyone lawyers up and life becomes very unpleasant for all involved.
And here's the thing: no anti-virus application is going to stop that from happening. There is no malware to be found here. Only users who have been stepped through the latest New-school Security Awareness Training will ensure that everyone's money stays where it's supposed to.
Free Phish Alert Button
When new spear phishing campaigns hit your organization, it is vital that IT staff be alerted immediately. One of the easiest ways to convert your employees from potential targets and victims into allies and partners in the fight against cybercrime is to roll out KnowBe4's free Phish Alert Button to your employees' desktops. Once installed, the Phish Alert Button allows your users on the front lines to sound the alarm when suspicious and potentially dangerous phishing emails slip past the other layers of protection your organization relies on to keep the bad guys at bay.

Don't like to click on redirected links? Cut & Paste this link in your browser:
















