 Researchers at Tessian have published a report looking at recent trends in spear phishing attacks. The researchers found that 45% of employees said that they clicked on a phishing email while they were distracted, and 52% admitted that they make more mistakes when they’re stressed. They also determined that most phishing emails are sent in the afternoon.
Researchers at Tessian have published a report looking at recent trends in spear phishing attacks. The researchers found that 45% of employees said that they clicked on a phishing email while they were distracted, and 52% admitted that they make more mistakes when they’re stressed. They also determined that most phishing emails are sent in the afternoon.
“The most malicious emails are delivered around 2PM and 6PM, with very little fluctuation day-to-day (except over the weekend),” the researchers write. “This isn’t an accident. Since employees are more likely to make mistakes when they’re stressed, tired, and distracted, the second half of the workday is a bad actor’s best bet.
This is reinforced by the fact that employees are most likely to mark an email as malicious between 9AM and 1PM, before the afternoon slump. We then see a steady decline starting at 2PM, right when the bad guys are ramping up.”
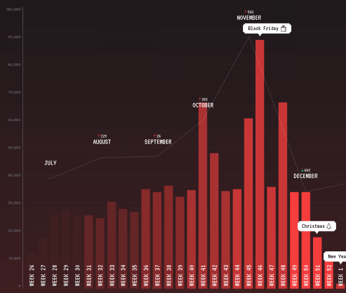
The report hints that cyber criminals are doing all they can to catch their victims - most of the emails were sent during the holiday season in Q4 2020, with the last three months of the year seeing 45% more malicious emails compared to the quarter before.
The researchers also found that organizations of different sizes offer different pros and cons for attackers: larger organizations can provide a larger payout, while smaller ones are often easier to break into.
“In terms of company size, bad actors will take whatever they can get,” the researchers write. “Wondering why they don’t focus exclusively on the ‘big fish’ (i.e. enterprise)? Because smaller companies – who generally have less money to spend on cybersecurity – are often easier to infiltrate. This can be a foothold for lateral movement, especially for companies with large supply chains.”
Tessian adds that attackers have a wealth of resources at their disposal to craft targeted social engineering attacks. “Between social media, OOO messages, and (free) online tools, it’s impossibly easy for bad actors to research their targets,” Tessian says. “Armed with information about a person’s company, colleagues, and personal life, they’ll be able to craft personalized, convincing, and effective email campaigns to trick them into handing over sensitive information or transferring funds.”
New-school security awareness training can give your organization an essential layer of defense by teaching your employees how to recognize sophisticated social engineering attacks. Tessian has the full story: https://www.tessian.com/research/spear-phishing-threat-landscape/
 Here's how it works:
Here's how it works:




