The FBI and Microsoft have issued a new alert, a warning of hybrid targeted ransomware attacks that attempt to encrypt an organization’s entire network. This is a new approach where criminal hackers penetrate the network, wipe out all backups, and infect all key machines. They use a little-known strain of ransomware called "Samas" which was first discovered in 2014. The majority of infections are detected in North America, and a few instances in Europe.
It is not clear yet if the current attack starts with phishing emails which infect a single workstation with ransomware and a Trojan that allows the hackers into the network, or if the network gets penetrated first and subsequently gets infected. It could very well be that both attack vectors are used, as Microsoft states that first an attack-scan gets launched, looking for vulnerabilities, and then malware gets deployed using the PSEXEC tool as per this schematic:
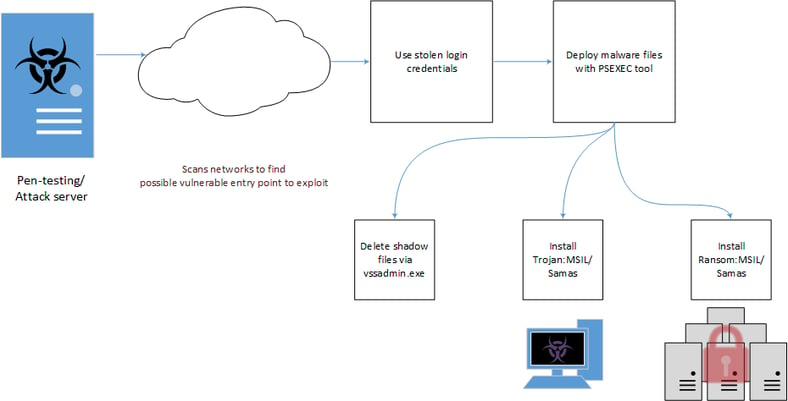
The FBI wrote the first alert Feb 18, 2016, and Microsoft published a technical analysis on March 17, 2016. They offer some mitigation and prevention hints and tips like disabling the loading of macros in Office programs through Group Policy settings like we suggested last month.
IntelSecurity also published a PDF in February with more details about this hybrid attack. The FBI calls it an "aggressive campaign" which initially targeted vulnerable JBOSS applications allowing the hackers in and then infecting the network.
Intel said: "During the past few weeks, we have received information about a new campaign of targeted ransomware attacks. Instead of the normal modus operandi (phishing attacks or drive-by downloads that lead to automatic execution of ransomware), the attackers gained persistent access to the victim’s network through vulnerability exploitation and spread their access to any connected systems that they could. On each system several tools were used to find, encrypt, and delete the original files as well as any backups.
These tools included utilities from Microsoft Sysinternals and parts of open-source projects. After the encryption of the files, a ransom note appears, demanding a payment in Bitcoins to retrieve the files. By separating particular functions from the ransomware binary, executing certain actions using free available tools and scripts, the adversaries tried to avoid detection as much as possible. This is unlike most ransomware cases that spread wherever possible. Targeted ransomware attacks have arrived." (Emphasis added).
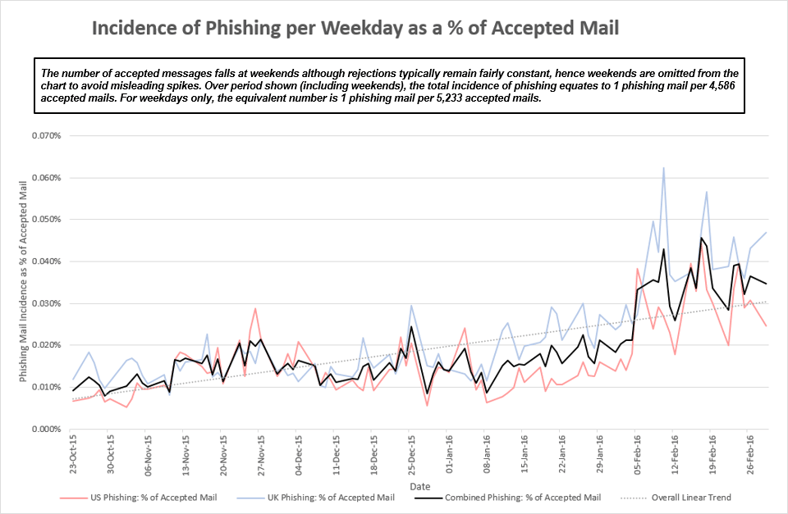
Phishing attacks are increasing these last three months, and ransomware attacks have seen tremendous growth since the beginning of the year.
Here is a Mimecast Review of Customer Traffic Patterns Across U.S.- and U.K.-Based Traffic From 23 October 2015 Through 26 February 2016:
Get the most informative and complete ransomware hostage rescue manual.
This manual is packed with actionable info that you need to prevent infections, and what to do when you are hit.
Related Pages: Ransomware





