 Since the publication of our first two blog pieces documenting the flood of Coronavirus-themed emails (see HERE and HERE), customers using the Phish Alert Button (PAB) have continued to share an ever-growing variety of emails from bad actors looking to capitalize on the crisis.
Since the publication of our first two blog pieces documenting the flood of Coronavirus-themed emails (see HERE and HERE), customers using the Phish Alert Button (PAB) have continued to share an ever-growing variety of emails from bad actors looking to capitalize on the crisis.
There are some rather unusual social engineering schemes being employed in some of these new phishes. The last one (spoofing Air Canada) just about caused me to fall out of my chair. Still shaking my head over that one.
So, once again, we are offering up a selection of those emails here so that IT administrators and users can see for themselves what these scams look like.
The Tried & True
Spoofs of authoritative sources of information continue to be the most common malicious virus-themed emails that are reported to us. And the top three spoofed organizations remain the CDC (Centers for Disease Control)...
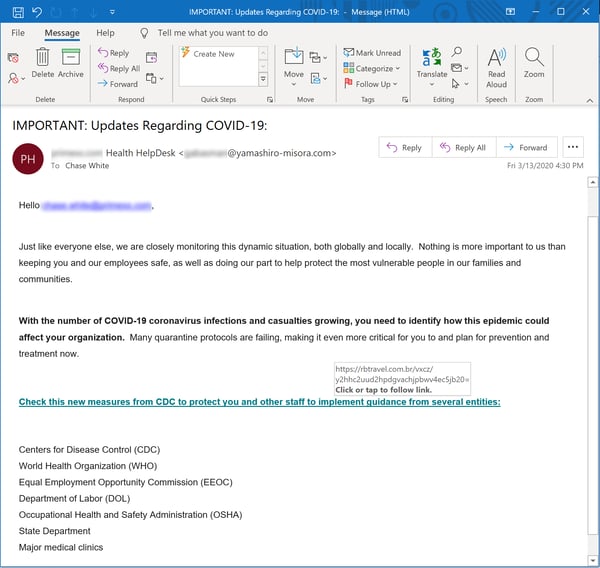
...the WHO (World Health Organization)...
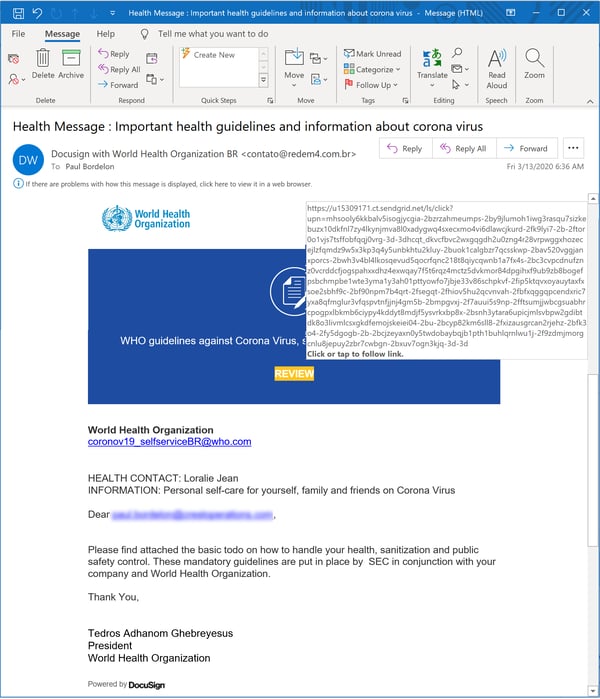
...and HR:
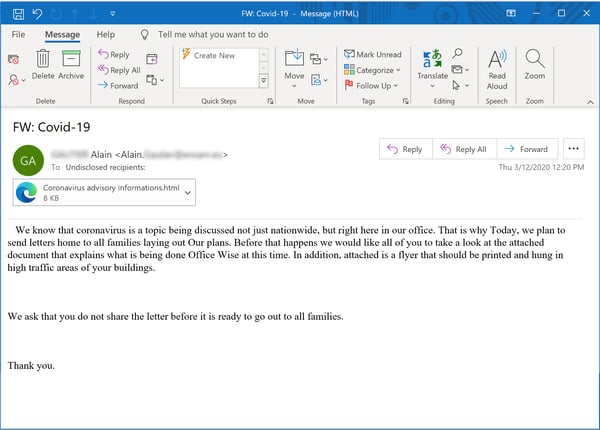
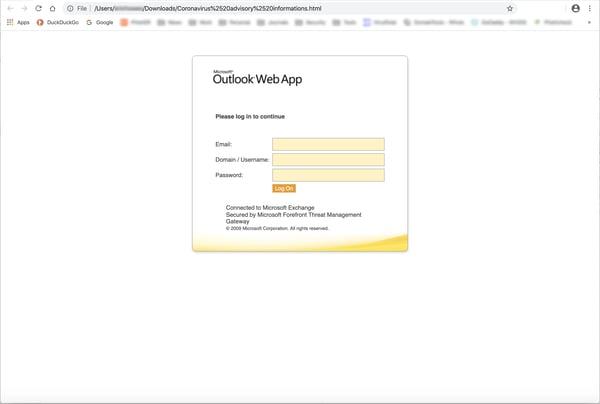
As with the earlier spoofs we reported, all three of these more recent emails lead to credentials phishes. The third (from HR) does take a bit of a novel approach, however, instructing recipients to download an attachment billed as an informational poster or flyer to be displayed on walls within the organization. The alleged poster/flyer is, in reality, just a standard credentials phish.
It's also worth pointing out that the second email above (the WHO spoof) not only spoofs Docusign (a frequent target of malicious spoofs) as well as the World Health Organization, but was delivered through Sendgrid, a well-known email service provider widely used by many companies and organizations.
This isn't the first time we've seen a malicious email campaign executed via what is almost certainly a compromised Sendgrid account (we also regularly encounter malicious emails phishing for Sendgrid account credentials). Indeed, malicious emails delivered through Sendgrid are becoming more and more common -- a worrisome trend, given that Sendgrid is likely whitelisted within many organizations, allowing emails delivered via that service to sail right through firewalls and email filtering services straight into users' inboxes.
The New & Novel
As we have stressed repeatedly in this space, the bad guys are always innovating -- always trying new approaches and experimenting with new social engineering schemes. In the days since our last blog post on this subject, we've seen some rather striking and even unusual attempts to trick users into clicking through to malicious content. As might be expected, some of these newer social engineering schemes seem to work better than others.
As has been widely reported, malicious actors are now using a Coronavirus/COVID-19 dashboard -- complete with a live map similar to the real thing built by folks at John Hopkins University -- to lure users to sites that install malware of one sort or another.
This particular email spoofs HHS (the U.S. Department of Health & Human Services) to dangle a link to that malicious map application in front of users desperate for the latest information on the spread of the virus.
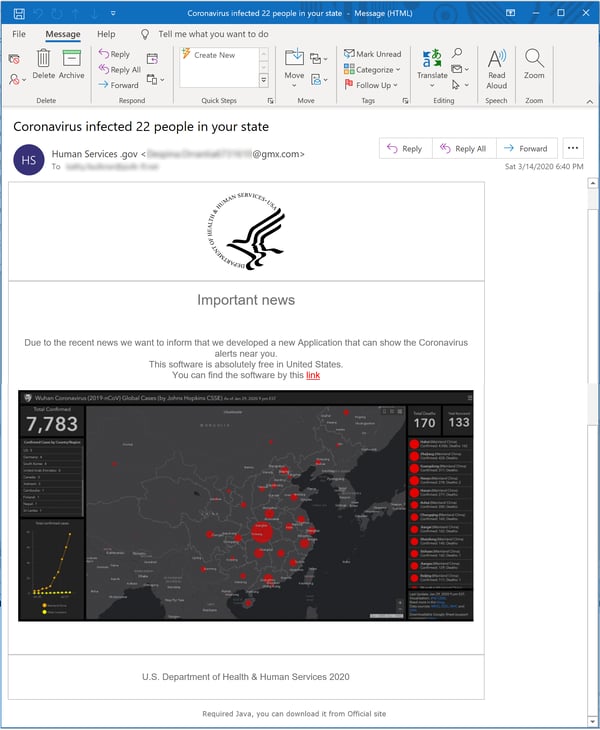
Although governmental agencies and organizations are the preferred targets for spoofing in virus-themed phishing emails, private companies are not above being targeted as well.
In this malicious email the bad guys spoof the well-known health insurance giant Cigna to hit users with a fake bill for "Coronavirus (COVID-19) insurance coverage."
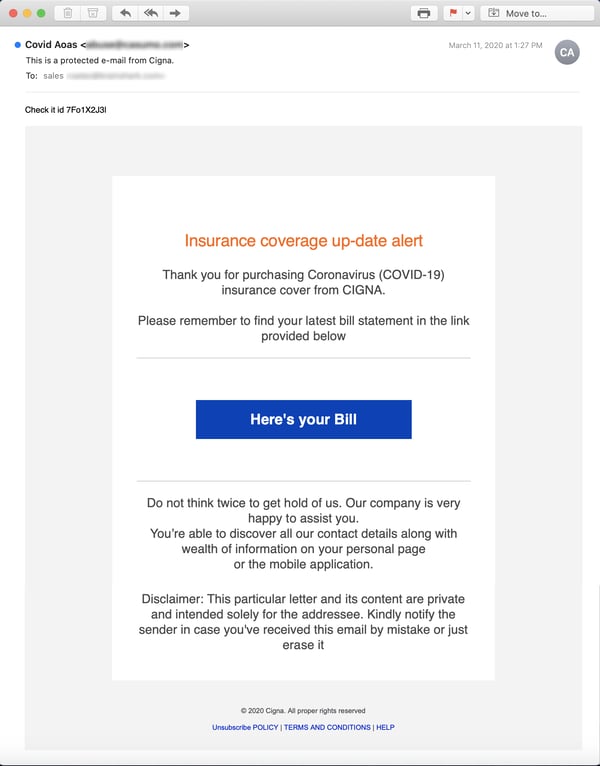
One might well wonder whether this is a viable approach. We don't know at this point. Despite the fact the many users will recognize the improbability of Cigna signing them up for insurance coverage against a pandemic without even bothering to ask, there could well plenty of freaked-out users who will immediately click that Big Blue Button to find out just what in the heck is going on. Some may even find such (fake) news welcome and comforting.
The Utterly Bizarre
And then there is this spoof of Air Canada, which...well, maybe you'd just better take a look for yourself.
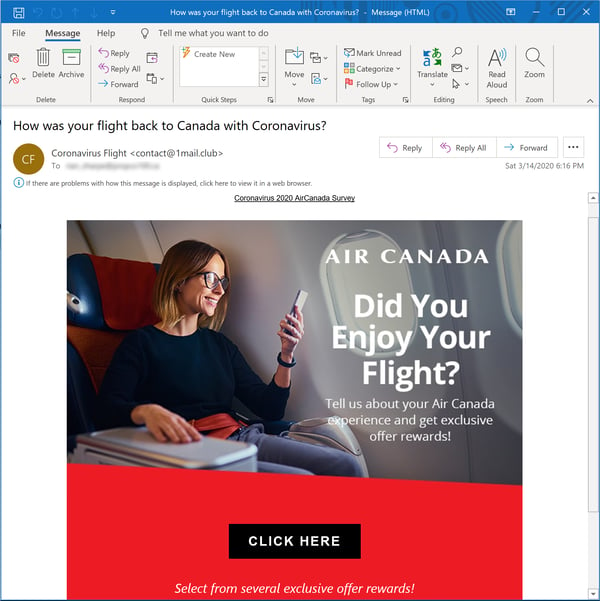
Well now. We've certainly seen Coronavirus survey emails before, both real and malicious (see our second blog post from last week). This one, however, is off the charts. The malicious actors behind this spoof either: a) have an unusually warped and evil sense of humor; b) have it in for the PR/Marketing folks at Air Canada (maybe the bad guys lost some frequent flyer points and weren't too happy about it?); or, c) are just completely clueless and tone deaf.
Whatever the case, we wouldn't expect many users to fall for this last phish. Then again, there's one in every crowd.
Conclusion
Good information and education remain the best disinfectants for malicious online schemes trailing in the wake of the Coronavirus itself. Unlike toilet paper, hand sanitizers, and medical masks, good information is not in short supply and not subject to panic buying at your local grocery store.
Our hope is that by letting concerned users actually see the COVID-19-themed phishing emails that the media is widely reporting they can make better, more informed choices about how to navigate the flood of information landing in their inboxes at this stressful moment. You can also check out our coronavirus phishing and security awareness resources to help keep your network secure while users are working from home.
 Here's how it works:
Here's how it works:




