| |
CyberheistNews Vol 4, 25
Editor's Corner

New Cellphone Phishing Hack Pulls Data Out Of Computer Over Air
This is the scariest news this month. Hackers can exfiltrate data via a cellphone and no longer need the Internet to invade and control a system, Ben Gurion University researchers say.
Using a technique called air-gap network hacking, all a hacker has to do is implant the right kind of malware into a cellphone that gets within range of a computer. Hackers anywhere in the world then use cellphone-based malware to remotely access any data they want, using the electromagnetic waves emanating from computer or server hardware, with no need for an Internet connection. It was not clear exactly what kind of cellphone they used during this research.
The concept of air-gap hacking is not new, but what’s new is the use of a cellphone to do it. Stuxnet was put on a thumbdrive to infect Iranian servers, and carried in. The new attack is light-years ahead of Stuxnet, because no physical contact is required to compromise a system. By the way, it's the reason that defense and intelligence agencies use TEMPEST spec hardware, see more at Wikipedia about using "leaking emanations" to spy on information systems:
http://en.wikipedia.org/wiki/Tempest_(codename)
How could a mobile phone be used to hack into an air-gapped network? In a take-off of an email phishing attack, a hacker could send an unsuspecting employee in a sensitive installation a text message that looks legitimate, but contains a link to malware that surreptitiously gets installed on their cellphone.
Once the malware is on the phone, it scans for electromagnetic waves which can be manipulated to build a network connection using FM frequencies to install a virus onto a workstation or server. The Ben Gurion University team has demonstrated how this is done with computer video cards and monitors. With the malware installed on the system, the phone connects to it via the FM frequency, sucks information out of the machine and uses the phone’s cellphone network connection to transmit the data back to hackers. All that’s needed is physical proximity to the system. The team said that one to six meters (3-18 ft) is enough.
Right now, the researchers said, there’s little that can be done to prevent this kind of cyber-attack other than turning off the phone. And that is exactly the reason that you are not allowed to take cellphones into highly secure areas. I'm sure the NSA has been playing with this as well. However, leaving your phone at reception is not a practical solution for the office, so the researchers are looking for other ways around this. It’s a major security risk, they said.
Until a solution is found, that risk will only increase, as news of this exploit spreads in the hacker community, and cyber criminals are going to replicate this for their own fun and profit. Just knowing it can be done is sometimes enough...
Another reason for effective Security Awareness Training, as all this starts with simple social engineering via a cellphone. By the way, KnowBe4 has a special 15-min module for Mobile Device Security you can step your users through:
http://info.knowbe4.com/mobile-security-module
Link to the source article in the Times of Israel:
http://www.timesofisrael.com/with-new-hack-cellphone-can-get-data-out-of-computers/
Make 30 Bucks In 5 Minutes & Keep Your Family Safe Online
I need your help for 5 minutes to get visibility on the current situation with ransomware like CryptoLocker and its copycats. And instead of just one person making a chance to win a prize, with this survey everyone that fills it out gets our $29.95 Kevin Mitnick Home Internet Course at no cost. Survey results in the next issue!
http://home.knowbe4.com/
Please, right away as you read this, click on the link below, and answer these quick multiple choice questions. I will send you your key to start the 8-module, 1-hour training ASAP. This key also allows you to invite 5 remote friends or relatives and share the course!
Please do this right now? Thanks so much in advance!!
https://www.surveymonkey.com/s/ransomware
Stand-alone CryptoLocker Variant Found
It looks like the Russian evil genius behind CryptoLocker, Evgeniy Mikhailovich Bogachev, has not been sitting still since the recent international law enforcement "Operation Tovar" which took over most of his botnet. A new strain of the infamous CryptoLocker ransomware has been found. The new Trojan does not rely on the 2048-bit RSA encryption and does not need any communication with a Command & Control server. It operates stand-alone, and the extensions of affected files are switched to .CRYPTOLOCKER.
A post at the Fakebit blog shows an analysis of a CryptoLocker spin-off which instructs the victim to access a location in the Tor network to receive details about the ransom payment. The Trojan encrypts data on the affected computer, but uses an encryption method that is weaker than the original and can possibly can be broken in order to regain access to the locked files:
http://fakebit.com/symmetric-encryption-in-a-cryptolocker-variant/
Judging by the choice of the encryption algorithm and the method for receiving payment, this CryptoLocker variant can be considered a not as strong as the original; but nonetheless, it does encrypt all the files it can get its hands on, and by relying on the original CryptoLocker brand name, these miscreants could still make some serious money.
More copycat ransomware will show up its ugly head this year. Law enforcement recommends not paying any ransom in order to discourage the criminal practices and you never know if they will keep their end of the bargain and provide the decryption. In some cases, it may make sense to do it anyway, in case of backups being unavailable of corrupted and months of work potentially lost.
In any case, stepping employees through effective Kevin Mitnick Security Awareness Training is a must these days. If you get a PO in before June 30, we will pay your ransom in case you get hit! Click Here:
http://info.knowbe4.com/we-will-pay-your-crypto-ransom
Quotes of the Week
"Be who you are and say what you feel because those who mind don't matter and those who matter don't mind." - Dr. Seuss
"I find that the harder I work, the more luck I seem to have." - Thomas Jefferson (1743-1826)
Thanks for reading CyberheistNews! Please forward to your friends. But if you want to unsubscribe,
you can do that right here
|

TODAY 2pm Webcast: How To Cut Audit Time And Audit Cost In Half
Regular Audit cycles are at the very least a pain in the neck, but often a severe disruption of normal IT work. And we are not even speaking of unexpected regulatory audits that may cause hefty fines.
Join KnowBe4 on TODAY at 2PM EDT to learn how to automate your compliance workflow so that you first become and then stay compliant, which will cut the normal time and costs needed for your audit cycle in half. You will learn about:
- Escaping from the Audit Cycle
- No More Spreadsheet Nightmares
- Centralizing Audit Evidence
- Managing Controls Testing
Register for this 30-minute KnowBe4 webcast HERE and plan to be part of the 15-minute online Q & A Session that follows. Hosted by KnowBe4's Brian Jack, CISSP, CEH:
http://info.knowbe4.com/webcast-knowbe4-compliance-manager-kcm-14-06-24

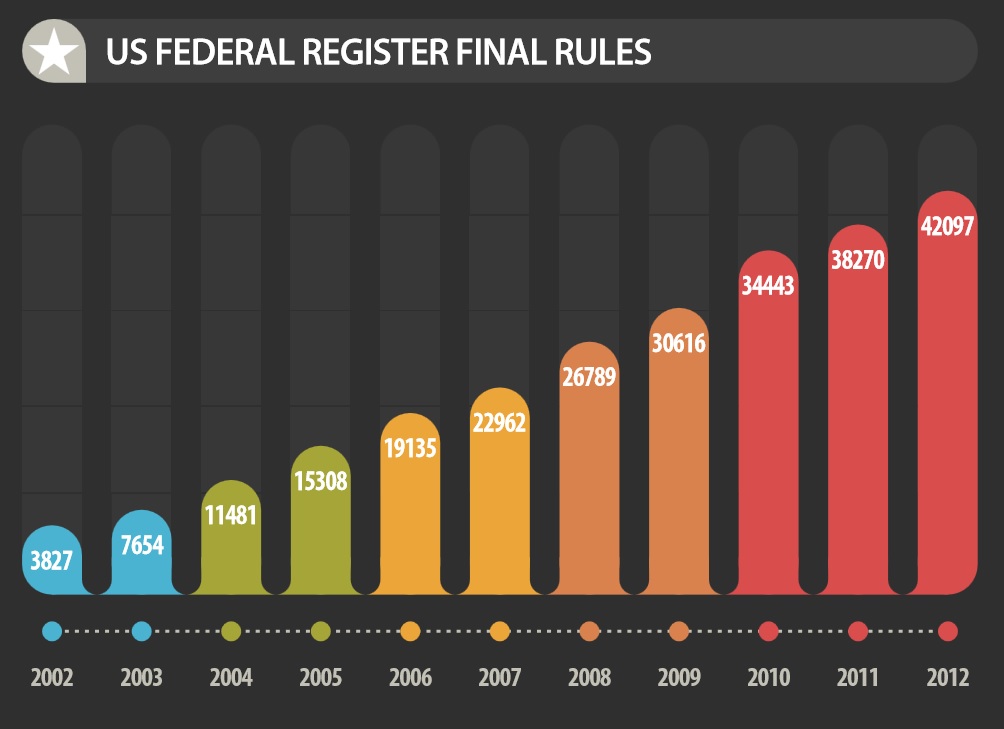
Federal Compliance Rules Skyrocket
Underscoring the difficulty of compliance management in the context of just US federal rulemaking – not to mention rules published by state, local and other governments and organizations – is the growth of the US Federal Register. This document, a daily publication that contains proposed and final regulations of US federal agencies, published an average of 3,827 final rules and 2,445 proposed rules each year between 2002 and 2012. That represents an average of 14.7 final rules and 9.4 proposed rules each workday. Managing this level of change using manual processes can be very difficult, if not impossible. Here is a pretty chart with the ugly numbers:

Oil Co. Wins $350,000 Cyberheist Settlement
A California oil company that sued its bank after being robbed of $350,000 in a 2011 cyberheist has won a settlement that effectively reimbursed the firm for the stolen funds.
TRC Operating Co. Inc., an oil production firm based in Taft, Calif., had its online accounts hijacked after an account takeover that started late in the day on Friday, November 10, 2011. In the ensuing five days, the thieves would send a dozen fraudulent wires out of the company’s operating accounts, siphoning nearly $3.5 million to accounts in Ukraine. Dennis Woods, founder and CEO of United Security Bank, said the hack took place on TRC’s computers — not the bank’s — after an employee at TRC fell for a phishing scam.
To quote Brian Krebs: "Lawyers, banks and oil companies. Many readers no doubt will have trouble shedding a tear for any of the parties involved in this dispute. But those who own their own businesses should take heed: Banking online carries serious risks. As we have seen time and again, a single virus infection can ruin your company. And I wouldn’t count on the lawyers to save your firm from the very real cost of a cyberheist: These court challenges can just as easily end up costing the victim business well more than their original loss." Full Story here:
http://krebsonsecurity.com/2014/06/oil-co-wins-350000-cyberheist-settlement/

Study: "Human Error" Contributes To Nearly All Cyber Incidents
Even though organizations may have all of the bells and whistles needed in their data security arsenal, it's the human element that continues to fuel cyber incidents occurring, according to one recent study.
The “IBM Security Services 2014 Cyber Security Intelligence Index,” a report that includes cyber security data on close to 1,000 of IBM Security Services' clients located in 133 countries, indicates that “human error” is involved in more than 95 percent of the security incidents investigated in 2013.
The most prevalent form involves clicking on a malicious link found in a phishing message, while other forms include system misconfiguration, poor patch management, the use of default usernames and passwords – or using poor passwords – as well as lost laptops or mobile devices, according to the report. Article with link to report at SC Mag:
http://www.scmagazine.com/human-error-contributes-to-nearly-all-cyber-incidents-study-finds/article/356015/

Cyberheist 'FAVE' LINKS:
* This Week's Links We Like. Tips, Hints And Fun Stuff.
OK Go's Music Video for their new song 'The Writing’s On The Wall' was all recorded in one take. You can watch this a few times!
http://www.flixxy.com/ok-go-s-new-music-video-is-a-feast-of-optical-illusions.htm?utm_source=4
Photographer Benjamin Von Wong does an underwater fashion shoot at a sunken ship off the coast of Bali:
http://www.flixxy.com/epic-underwater-photoshoot-the-secret-to-success.htm?utm_source=nl
Parody of the adorable Volkswagen Super Bowl commercial that starred a little boy dressed as Darth Vader trying to harness the power of the force:
https://www.youtube.com/watch?v=EPNjWWQqWCA
A Brazilian man shows an easy method to climb up a palm tree in the Amazon rainforest ... and an astonishing way to come down rapidly:
http://www.flixxy.com/old-man-shows-off-trick-for-climbing-trees.htm?utm_source=4
A black bear follows two men jogging on the trails near Fort McMurray, Alberta, Canada. This bear is persistent (or hungry)!:
http://www.flixxy.com/black-bear-tails-joggers.htm?utm_source=4
Talking about bears, Drew Hamilton has a close encounter with a Coastal Brown Bear while camping at the McNeil River State Game Sanctuary, Alaska. Can you spot the other 20 or so bears in the video?:
http://www.flixxy.com/close-encounter-of-the-brown-bear-kind.htm?utm_source=4
Given a round tea-cake and two persons of moderate appetite to eat it, how should it be cut so as to leave a minimum of exposed surface to become dry?:
http://www.flixxy.com/the-scientific-way-to-cut-a-cake.htm?utm_source=4
From the archives - Baby Laughing. Try NOT to laugh when you see this:
https://www.youtube.com/watch?v=UjXi6X-moxE
These 21 Gorgeous Homes Were Made From Cheap, Old, Rusty Shipping Containers!:
http://www.reshareworthy.com/amazing-shipping-container-homes/
|
|

