 If you have sales offices in Europe, or full subsidiaries, you need to be aware of the NIS directive. Peter Dekker at Enisa warned about the following:
If you have sales offices in Europe, or full subsidiaries, you need to be aware of the NIS directive. Peter Dekker at Enisa warned about the following:
During 2017, the GDPR buzz reached peak intensity, however, all that noise drowned out another, arguably even more important upcoming EU law: The Network and Information Security (NIS) Directive.
The NIS Directive is the first piece of EU-wide legislation on cybersecurity and, by May 9, 2018, all EU member countries will have to have it incorporated it into their own national laws.
GDPR and privacy are important, but the NIS Directive has a wider scope and actually deserves more attention than the GDPR. Why?
The NIS Directive Focuses On Critical Infrastructure
2017 showed us what's at stake. WannaCry paralyzed hospitals across the UK, and affected organizations across the world. A bit later, NotPetya disrupted a Ukrainian nuclear plant and EU transport companies like TNT and Maersk.
Then, in the summer, half a million patients were told to go back to the hospital, because their pacemakers were hackable due to software vulnerabilities.
The NIS Directive aims to improve cybersecurity in three areas:
1. National cybersecurity capabilities of the individual EU countries (e.g. they must have a national CSIRT, perform cyber exercises, etc.)
2. Cross-border collaboration between EU countries (e.g. the operational EU CSIRT network, the strategic NIS cooperation group, etc.)
3. National cybersecurity oversight of the critical sectors, ex ante for operators in critical sectors (energy, transport, water, health, finance, etc.) and ex post for critical digital service providers (internet exchange points, domain name systems, etc).
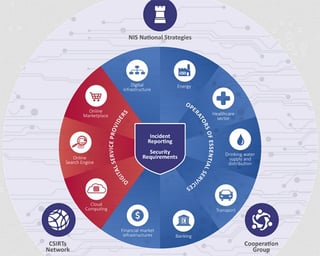
You can read more about the directive in this short factsheet, published by the European Commission. The snippet below, taken from an ENISA poster, gives a visual overview.

Prepare yourself
Of course, many EU countries already have some of the pieces of the puzzle in place. Many countries already have a national CSIRT, conduct cyber exercises, and have national legislation in place for the protection of critical information infrastructure.
Still, there’s no doubt that 2018 will be a promising and challenging year for cybersecurity in Europe, and cybersecurity professionals across the board should prepare for it.
National authorities and the operators of critical services will have to collaborate to set in motion an entirely new oversight mechanism – one that, for the first time, spans different sectors and crosses national borders.
Note that many EU countries did not wait for May 9 to start transposing and implementing the NIS Directive into national law. In the Netherlands, for example, a mandatory breach reporting law for critical sectors was adopted in 2017 and went into force on January 1, 2018.
Opportunities
The NIS Directive provides many opportunities that can help critical operators become more resilient. One of the nice things of the directive is that it is cross-sector and cross-border legislation, opening up the possibility to address cybersecurity issues that cut across.
For example, some years ago banks were suffering a lot of incidents due to specific types of DDoS attacks. For banks it was an unfortunate externality as most telecom providers simply did not care to filter out the unwanted (spoofed) traffic. The NIS Directive provides a framework to start a discussion with the regulators in another sector, substantiated with numbers about frequency and impact of incidents. This makes it easier to decide how a certain issue can be solved most efficiently (e.g. is it cheaper if banks invest in more DDoS protection, or should telecom providers implement better filters?).
Another cross-sector issue, and a growing concern in cybersecurity, is the emergence of circular dependencies between different critical sectors. For example, energy companies rely more and more on telecoms’ infrastructure and digital services for their operations, which in turn rely heavily on the power grid. Short disruptions of power supply can be overcome with batteries or diesel-powered generators, but during large disruptions, batteries and fuel run out. If one power plant blacks out, the rest of the grid can become unstable.
Blackouts in one country can quickly spread across to other countries. So to avoid a cascading effect it is necessary to arrange for priority truckloads with diesel fuel to refurnish critical data centres and telecom sites. This means a third critical sector (transport) comes into play, which, as we know, is also increasingly dependent on telecom and digital services.
Pitfalls
As with any type of legislation there are also pitfalls to avoid. It is important that this directive leads to practical results and real improvements in cyber resilience.
Since every sector has different issues, a theoretical one-size-fits-all approach would be ineffective. In sectors with low cybersecurity maturity, there will be a need to help organizations implement the cybersecurity basics, like patching of vulnerabilities. In other sectors, like finance or telecommunications, where cybersecurity maturity is high, other activities will be more useful. For an effective sector-specific approach it will be important to leverage the various national and EU-wide ISACs (Information Sharing and Analysis Centers), which are sectorial public-private partnerships where participants exchange cybersecurity information and experiences, on a voluntary basis.
When it comes to incident reporting it will be important to avoid needless formalities, and the so-called problem of the incident reporting graveyard, i.e. collecting information about incidents, only for it to be hardly used. Some cases will be interesting for critical infrastructure operators to dive into deeper, but will be of little interest for regulators, and vice versa. The information sharing happening in the ISACs is necessarily of a very different nature than the information sharing that happens as part of the mandatory breach reporting process managed by the national authorities.
Conclusion
2018 is the year of the NIS Directive and it is up to us, the cybersecurity community, to use our collective brains and wit to avoid the pitfalls and to exploit the many opportunities of this new cybersecurity legislation. As cybersecurity professionals we know better than anyone what is at stake. Let’s not wait to see bigger incidents and start the discussion now. The hashtag is #NISD.
Source: HelpNetSecurity




