 New whistleblower details surrounding the December 2020 attack on the cloud-enabled IoT device manufacturer paints a far worse picture than what was disclosed.
New whistleblower details surrounding the December 2020 attack on the cloud-enabled IoT device manufacturer paints a far worse picture than what was disclosed.
Cyberattacks almost seem like a daily occurrence, such that we’ve seen organizations notify customers with a “we’ve got everything under control”-sounding email with little to no repercussions.
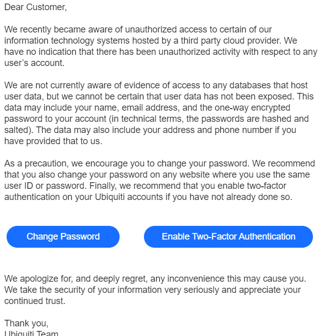
Such an attack on Ubiquiti occurred back in December of last year, and a notice was sent in January of this year notifying customers of the breach (link is to KrebsOnSecurity) while minimizing its impact, suggesting password changes and enabling 2FA.
Case closed, right?
Wrong. New details from a whistleblower bring to light the catastrophic nature of the attack. According to Krebs on Security, “The breach was massive, customer data was at risk, access to customers’ devices deployed in corporations and homes around the world was at risk.” With over 85 million networking infrastructure devices in over 200 countries worldwide, this attack put a major portion of the world at risk. According to the article, several Linux machines (with an undisclosed purpose) were setup in Ubiquiti’s AWS instance, backdoor administrative credentials were created, and Ubiquiti source code was allegedly stolen.
According to the whistleblower, administrative access to Ubiquiti’s servers hosted on Amazon Web Services all via a single IT employee who stored the admin credentials in LastPass.
While there are no details on specifically how those credentials were compromised, there’s a simple attack chain that would do the trick: Starts with a spear phishing attack targeting Ubiquiti IT staff. Use social engineering tactics to trick the IT-victim into infecting their machine without them knowing (we’ve seen examples of this previously). The malware installed includes a keylogger which eventually captures a visit and logon to LastPass. Assuming there’s no MFA on the IT staffers LastPass credential (something LastPass *does* support, BTW), and the bad guys have access to every credential stored within.
Given the attackers attempted to extort 50 BTC from Ubiquiti to keep quiet, it would make sense if this was, indeed, a targeted attack.
Kreb’s recommends a minimum of changing passwords on any Ubiquiti devices if you have any, and goes as far as to recommend deleting administrative profiles, updating firmware, and creating new profiles with different passwords.
In addition, the administrative access gained by a single IT employee highlights the need for every user – even IT staff – to undergo continual Security Awareness Training to ensure that should an attack begin with a phish, *every* user is prepared to easily identify malicious content and stop it in its tracks before an attack becomes catastrophic like this one.
 New-school Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn't a one and done deal, continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your quote for KnowBe4's security awareness training and simulated phishing platform and find out how affordable this is!
New-school Security Awareness Training is critical to enabling you and your IT staff to connect with users and help them make the right security decisions all of the time. This isn't a one and done deal, continuous training and simulated phishing are both needed to mobilize users as your last line of defense. Request your quote for KnowBe4's security awareness training and simulated phishing platform and find out how affordable this is!




