 By Eric Howes, KnowBe4's Principal Lab Researcher. Over the past month we have provided readers with regular updates on the growth and development of Coronavirus-themed phishing emails reported to us by customers using the Phish Alert Button (PAB). From the first wave of phishes spoofing recognized authorities like the CDC and WHO to the exponential growth of new, novel, and re-purposed phishing emails during the final two weeks of March, it's been a wild ride.
By Eric Howes, KnowBe4's Principal Lab Researcher. Over the past month we have provided readers with regular updates on the growth and development of Coronavirus-themed phishing emails reported to us by customers using the Phish Alert Button (PAB). From the first wave of phishes spoofing recognized authorities like the CDC and WHO to the exponential growth of new, novel, and re-purposed phishing emails during the final two weeks of March, it's been a wild ride.
Following that surge of malicious, virus-themed emails at the end of last month, malicious actors have been re-grouping -- pulling back on the use of re-purposed, older phishing templates while further refining social engineering approaches designed to exploit unique features and opportunities of the COVID-19 pandemic. In short, they are turning to what works.
As they have consolidated and honed their social engineering tactics in recent days the bad guys have demonstrated that they are very attuned to the uncomfortable, challenging, and occasionally bewildering day-to-day circumstances in which organizations and their employees have suddenly been forced to operate. Put another way, the bad guys know and understand their audience -- the users and employees now largely working from home, often struggling with unfamiliar technology, and understandably fretting over their own futures as well as what lies ahead for the organization.
So, after throwing everything and the kitchen sink at users over the last few weeks of March, malicious actors are now settling on social engineering schemes intended to hit employees where they live and, now, work. In what follows we'll take you through a collection of the latest phishing emails reported us by customers so that you can see just how the bad guys are working to convert every new challenge you and your employees are currently dealing with into an opportunity for themselves.
For explanatory purposes, we have grouped this collection of malicious emails into three loose piles.
IT Operations
The first should come as no surprise, for the mainstream news media has provided plenty of coverage to the travails encountered by employees and organizations making the transition to WFH (Work from Home) using software and services that facilitate a remotely connected, mobile workforce.
When users struggle to adopt new technologies into their day-to-day lives, opportunities abound for malicious actors -- and they go far beyond "Zoom-bombing" or the privacy shortcomings of some of these applications and services.
For starters, many users are now remotely connecting to their workplaces for the first time. The bad guys are perfectly prepared to step in and lead them astray, starting with a generous offer to provide them with a "technical foundation" for working remotely.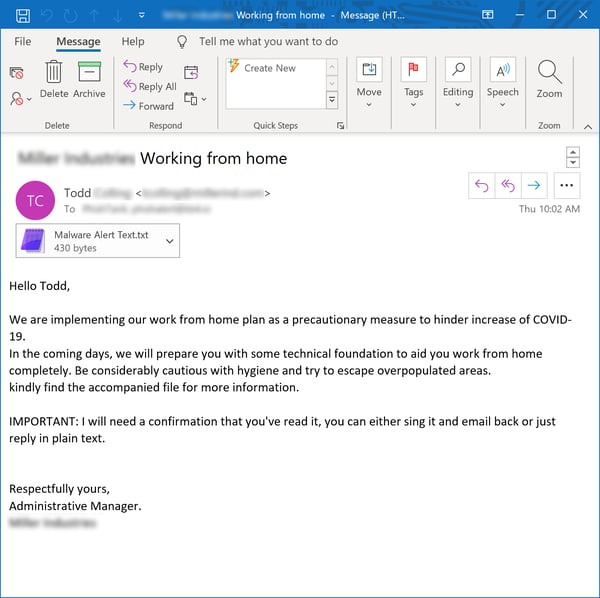
Once users are ready to connect they'll likely need to download software and step through some kind of process designed and approved by the organization itself.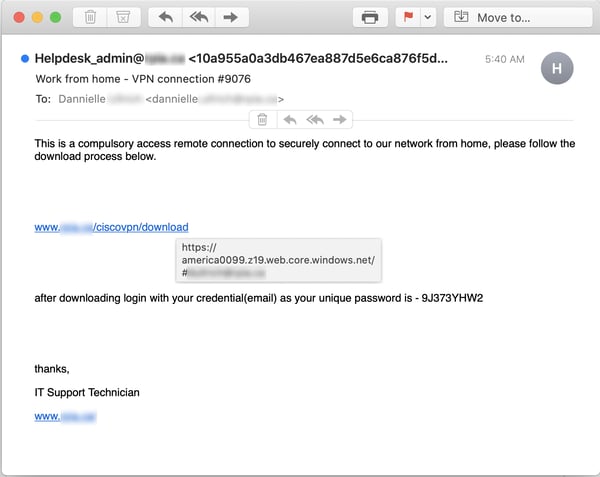
Many of these users will be connecting with a VPN for the first time.
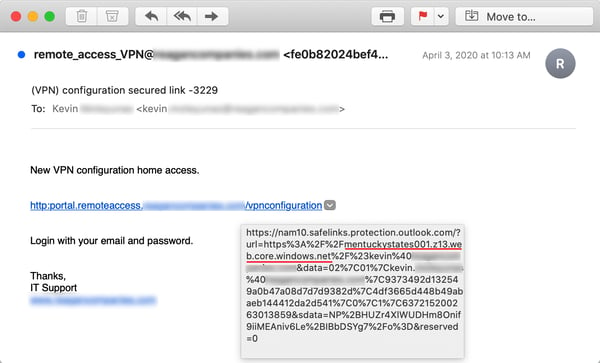
And many will likely not be surprised to encounter a login page hosted on a Microsoft domain like windows.net: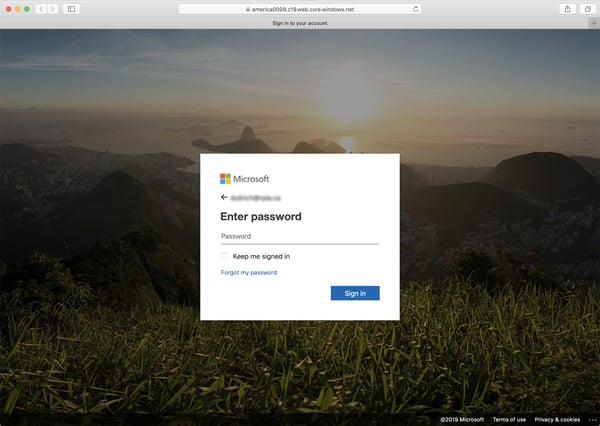
This Microsoft Azure domain has proven to be a favorite for malicious actors pushing these kinds of social engineering schemes, as it is the perfect cover for springing a credentials phish on users who are struggling just to get everything to work and would welcome anything that looks like familiar, solid ground.
Indeed, many organizations are now working diligently to do just that for remotely connected workers: provide them something resembling an online island of familiarity as well as a safe place to stay in touch with their organization.
Unsurprisingly, the bad guys have that angle covered as well: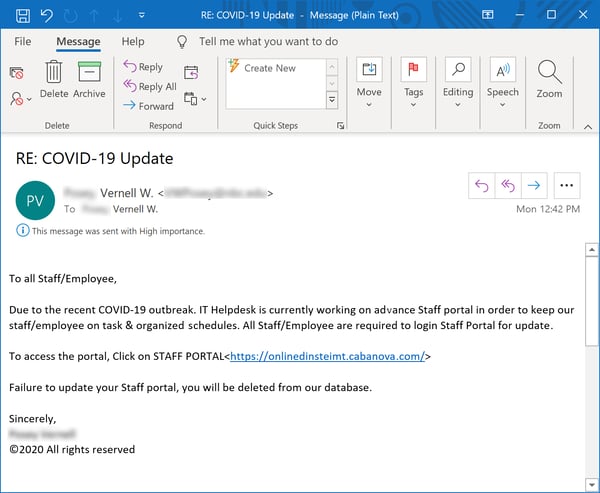
That gateway to home territory takes users to -- what else? -- another credentials phish...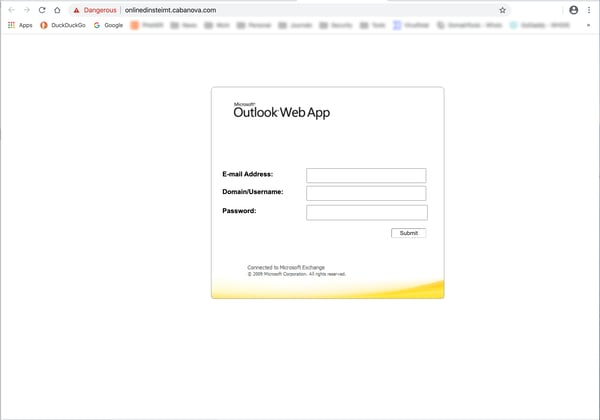
...enabling the bad guys to connect remotely to an organization's network right along with their employees.
Malicious actors are even happy to invite those employees to Zoom meetings: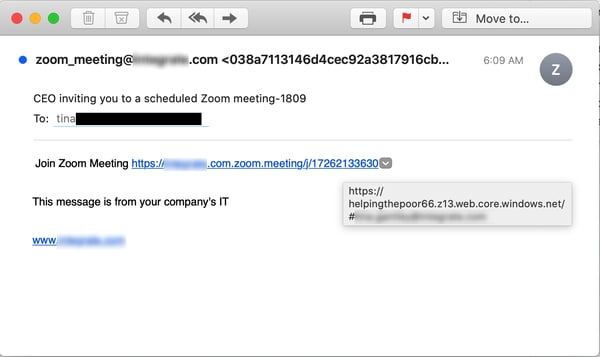
And, yes, users who take the bait will be required once again to step through a login process on the domain windows.net.
Keep in mind that we are still early days in this transformational crisis, and we fully expect malicious actors to steadily expand their repertoire of IT-themed phishing attacks.
Policies & Procedures
The transition to WFH involves more than getting Zoom installed on users' home PCs and taking them through the process of connecting to the office via the corporate VPN. Organizations are discovering that such a transition requires new policies and procedures to keep users on track, up to date with the latest news, and working productively. The bad guys, of course, have a full suite of social engineering schemes to do just that.
First up are new operational policies surrounding the WFH transition: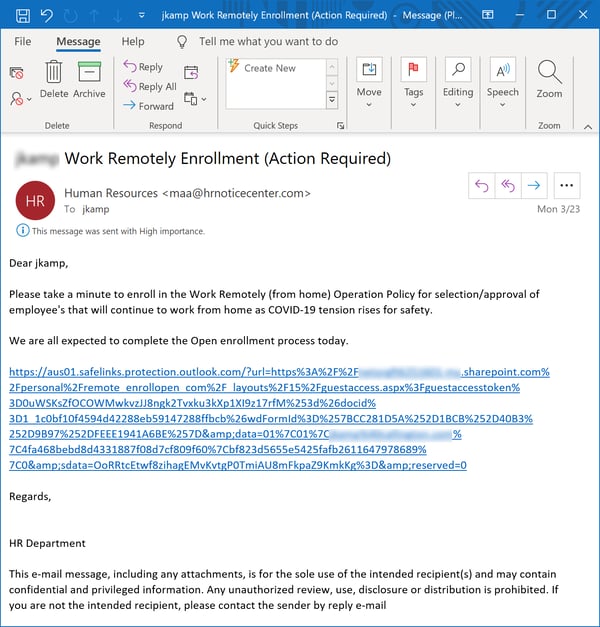
...which may well involve yet another credentials phish masquerading as a WFH enrollment process of some kind.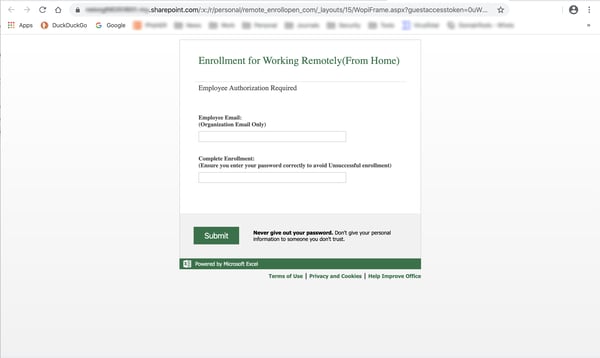
Users will be expecting to receive regular messaging from their employers about how the organization is navigating the COVID-19 crisis. Unsurprisingly, the bad guys have plenty of information and answers: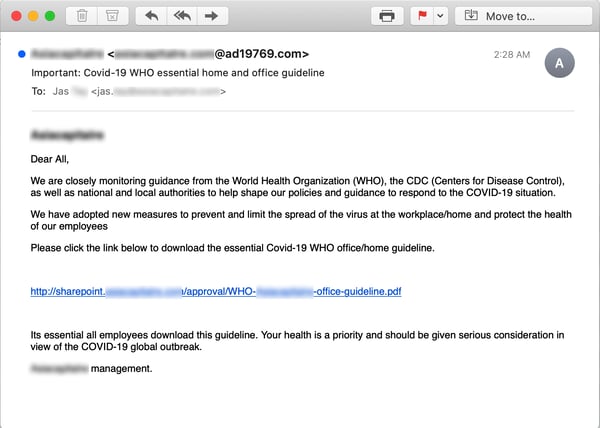
Those "guidelines" are even stored on the organization's (fake) instance of Sharepoint: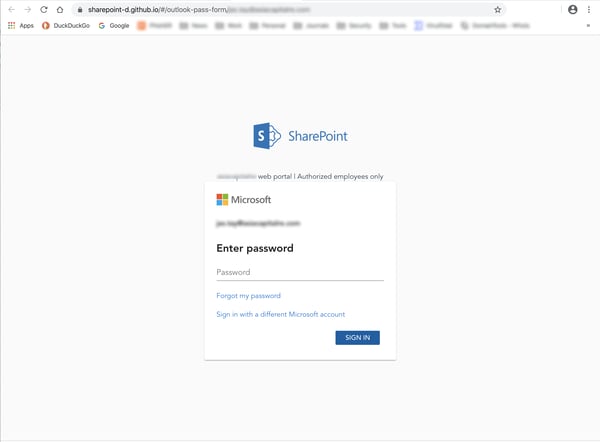
Communication is a two-way street, though, and malicious actors are well aware that organizations are now surveying their employees to keep on top of their needs and concerns.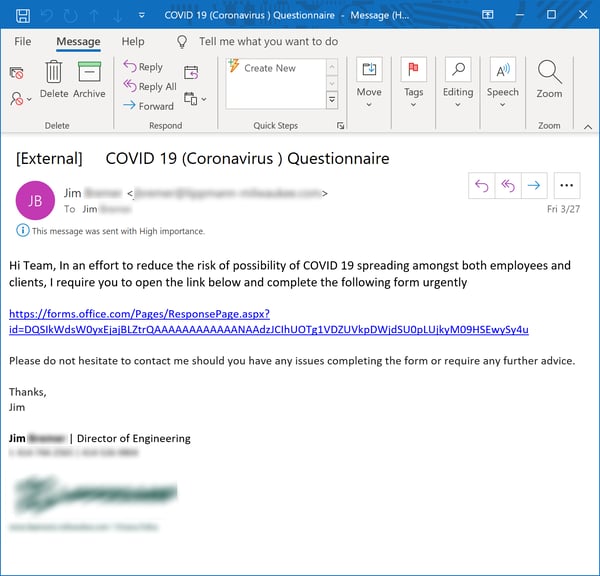
The "questionnaire" in this case -- appropriately hosted on Microsoft Forms -- was taken down by the time we took a look.
Right at the top of employees' list of concerns is, quite understandably, their own paycheck. And news such as this...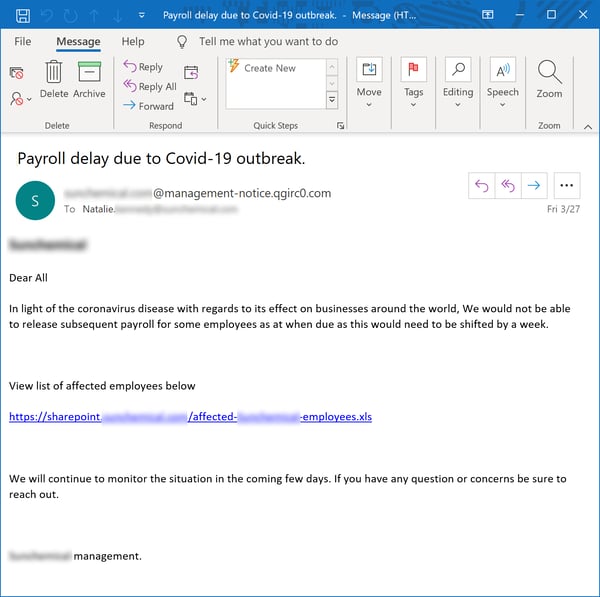
...is likely to spur more than a few clicks through to malicious content of one sort or another.
The bad guys, as it turns out, have a lot of experience targeting the payroll process, allowing them to exploit COVID-19 to take yet another run at the employees in your organization who actually handle the money for everyone else.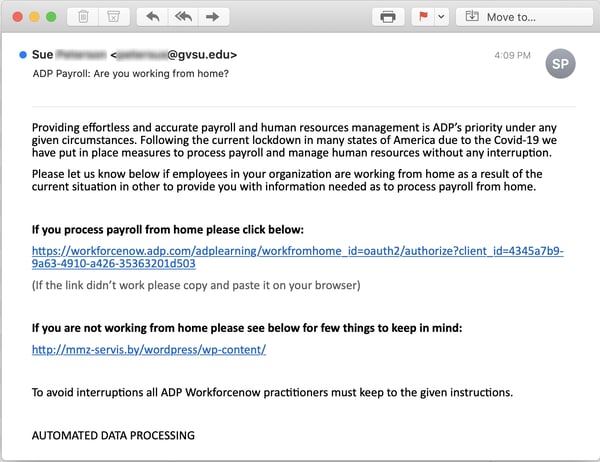
This spoof of ADP, a widely used HR platform, comes complete with a landing page custom designed to coax credentials out of the folks who do the heavy lifting in payroll.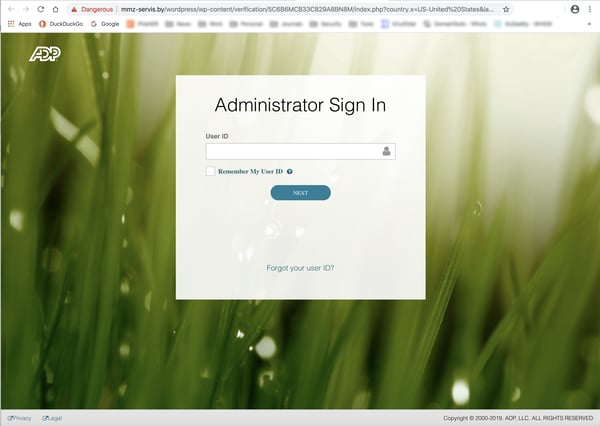
And you shouldn't be surprised to learn that malicious actors are completely up to speed on the Paycheck Protection Program that was included in the recently passed fiscal stimulus package for U.S. citizens and businesses. In fact, the growing confusion that has surrounded the roll-out of that program has provided threat actors the perfect opportunity to dangle hints of new information in front of senior members of your organization: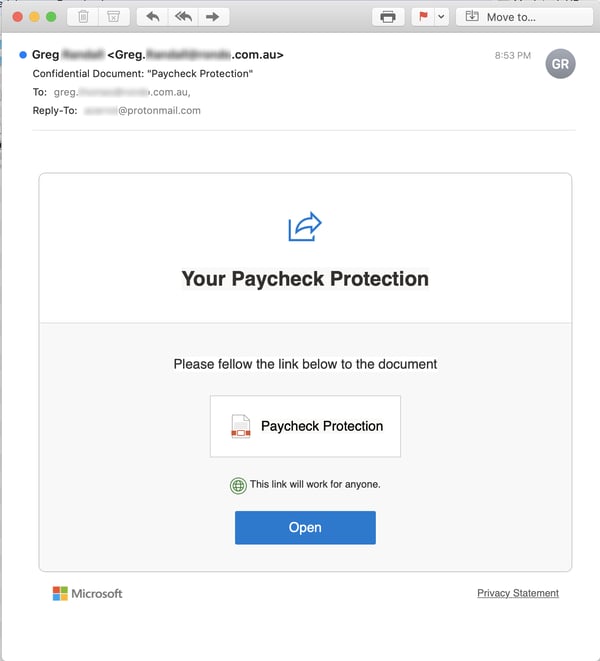
Yep, the above takes users once again to a Microsoft credentials phish.
As with the IT-themed phishes we looked at earlier, we expect the bad guys to continue developing social engineering schemes that seek to insert themselves into the digital back-and-froth between organizations and their remotely connected employees.
The Well-Being of the Workforce
Beyond their own paychecks, employees are very concerned about their own safety and well-being as well as that of their friends, families, and co-workers. Malicious actors have been exploiting these concerns from the very first blast of Coronavirus-themed phishing emails back in early February, which spoofed the CDC and WHO to trick users looking for more information on the pandemic into clicking malicious links.
That same ruse continues work -- esp. when said offers of information about the rising number of infections concern fellow employees: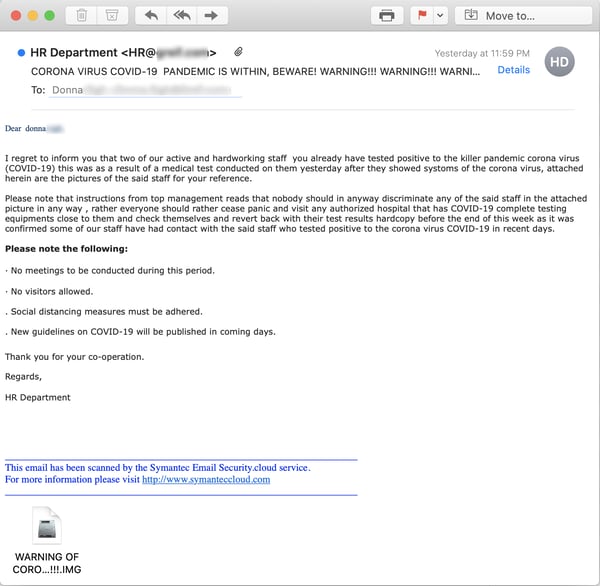
Although the vast majority of virus-themed phishing emails we've seen lead to credentials phishes, some do indeed lead to live executable malware -- often wrapped in .IMG files (a disk image archive format increasingly popular with the bad guys). And, like this one, the majority of that malware tends to consist of sophisticated backdoor trojans that allow malicious actors to quietly operate long-term inside a breached organization's network.
This particular social engineering scheme appears to be acquiring legs, as we have seen multiple versions of it just in the past week.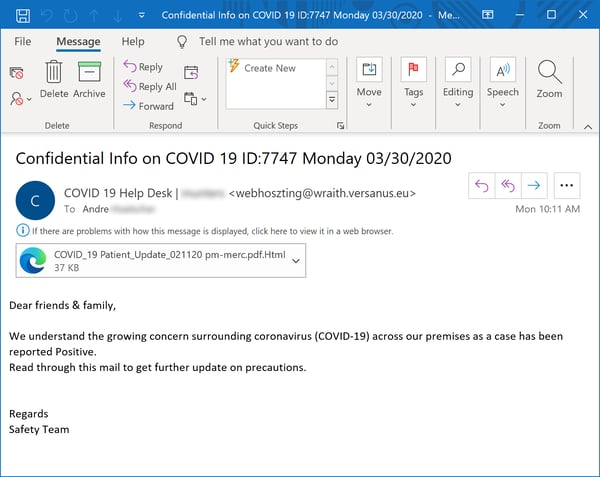
The attached HTML file is, as per usual, a credentials phish every bit as slick as those we looked at earlier.
From the very outset, information about the COVID-19 pandemic has proven to be not only that most sought after of commodities but the perfect tool to motivate anxious users into unthinking clicks on malicious content. Unfortunately, we do not expect this dynamic will change anytime soon.
Conclusion
The picture that is emerging from the most recent Coronavirus-themed phishing emails is one that should cause every organization to sit up and take note.
After initially resorting to "shock and awe" social engineering tactics designed to stampede panicked users into opening malicious links and attachments, malicious actors are now transitioning to phishing campaigns grounded in the day-to-day realities faced by disrupted organizations and their remotely connected users.
Now more than ever your users need to be educated and trained to handle this onslaught of cleverly designed and smartly executed phishing campaigns. Failing that, you may well find yourself with some unexpected guests on your organization's network -- guests skilled and experienced at making their residence inside that network a most profitable one.
 Here's how it works:
Here's how it works:
