Late last year we reported that Microsoft Sway, an online presentation program, was being exploited by malicious actors to host malicious files used in phishing attacks. Since then, customers using the Phish Alert Button (PAB) have reported a dramatically fewer number of phishing attacks using files created and hosted on Sway. Unfortunately, the bad guys seem to have found a solid replacement: Canva, one of Australia's more successful tech companies.
So, what is Canva anyway? Canva is typically described as a "graphic design platform" that
allows users to create social media graphics, presentations, posters and other visual content. It is available on web and mobile, and integrates millions of images, fonts, templates and illustrations. Users can choose from many professional designed templates, and edit the designs and upload their own photos through a drag and drop interface. The platform is free to use, and paid subscriptions like Canva Pro and Canva for Enterprise offer additional functionality. Users can also pay for physical products to be printed and shipped.
In short, Canva appears to offer bad guys a functional replacement for Microsoft Sway, allowing them to design and hosts malicious files that can employed in phishing attacks against unsuspecting users -- credentials phishes, for the most part -- though without quite the same brand awareness and trust engendered by Microsoft's Office platform.
In what follows we'll step you through some common examples of phishing emails that are regularly reported and that use Canva to spring credentials phishes on users through a variety of common social engineering schemes.
What's On the Menu? (Hint: the Usual Fare)
As noted above, Canva is primarily used by malicious actors to create and host malicious files that redirect users to credentials phishes hosted elsewhere on the internet. A Canva-based phishing attack usually takes the form of a three-step process commonly employed with other online services that are frequently exploited.
Let's look first at a very recent example. This particular phishing attack opens with an email clearly designed to spoof a file sharing notification from Microsoft Sharepoint:
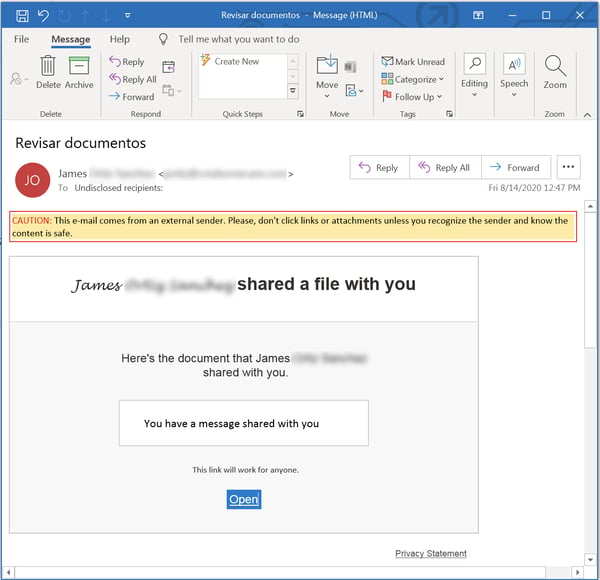
As spoofed emails go, this isn't a bad one, though key brand names that could have been used to sell the ruse and build credibility with users are omitted.
The link for the blue "Open" button takes users to a rather unusual-looking document or file hosted on Canva:
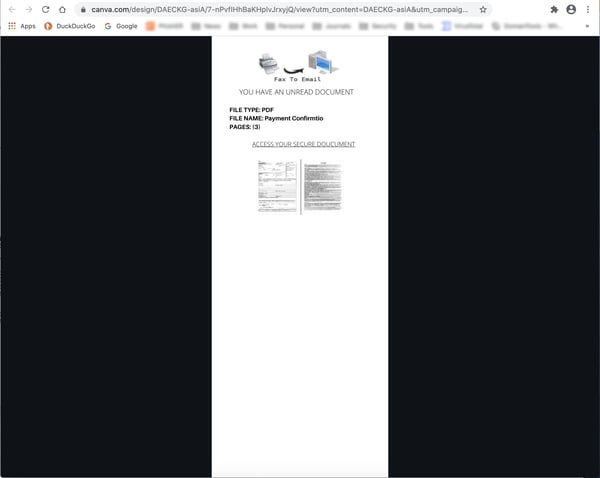
The odd appearance of this document ought to alert users that something is amiss. If nothing else, this clearly isn't anything hosted on Sharepoint. Users who elect to plow on in an attempt to access the "Secure Document" are shuffled off to a poorly spoofed Sharepoint login page hosted on Weebly:

Although the bad actors behind this phish finally manage to drop some branding clues, the effort is marred by the advertisement at the bottom of the page. Will users even notice, though?
Although Microsoft is by far the brand we see most commonly spoofed in Canva-based phishing emails, Docusign is a close second.
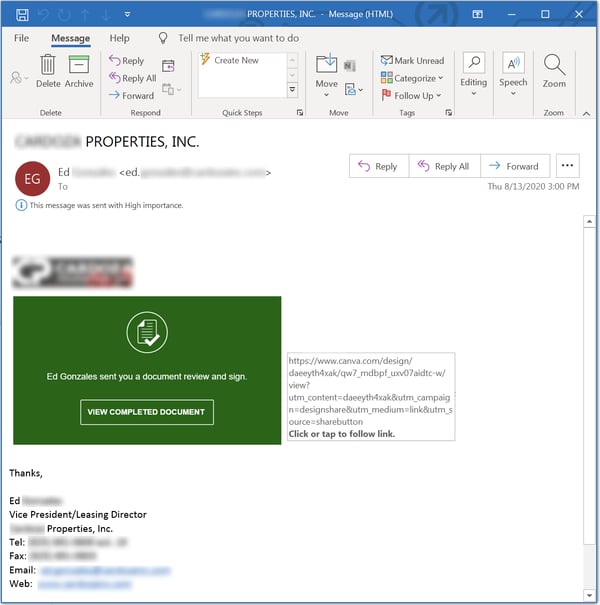
Again, this isn't the slickest Docusign spoof we've seen, but for many users it may be good enough to click through to this document hosted on Canva:
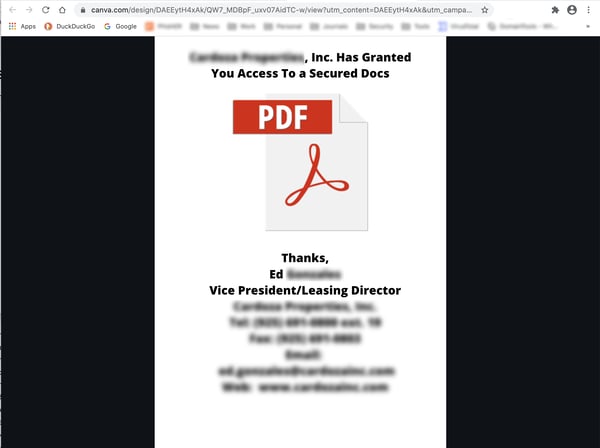
As with the Sharepoint spoof above, this second document -- which bears no resemblance to a secure document being served up by Docusign -- functions only as a waypoint on the road to the final destination: another credentials phish.
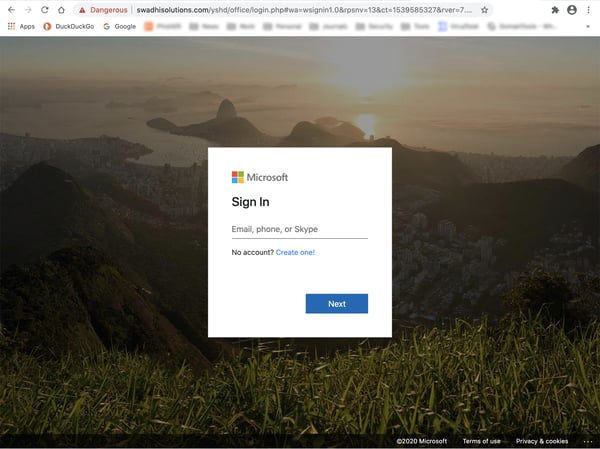
Now, this particular credentials phish is rather well done. The problem here, of course, is that a spoofed Microsoft login page is wildly inappropriate for a phishing attack that led off with a spoofed Docusign email. This kind of brand mismatch is something we often encounter in phishing emails.
While spoofs of Microsoft and Docusign are common enough in Canva-based phishing attacks, the malicious emails sporting Canva links that we most frequently encounter are fake voice mail notifications -- a genre that has been on the rise over the past few months. Strangely, the initial email in this particular attack immediately requires users to open yet another attached email:
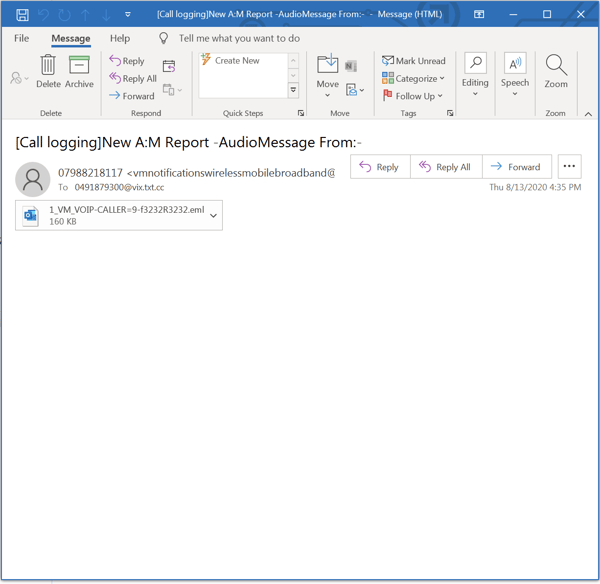
The attachment itself, which claims to be a notification from Vodaphone, redirects users to Canva...
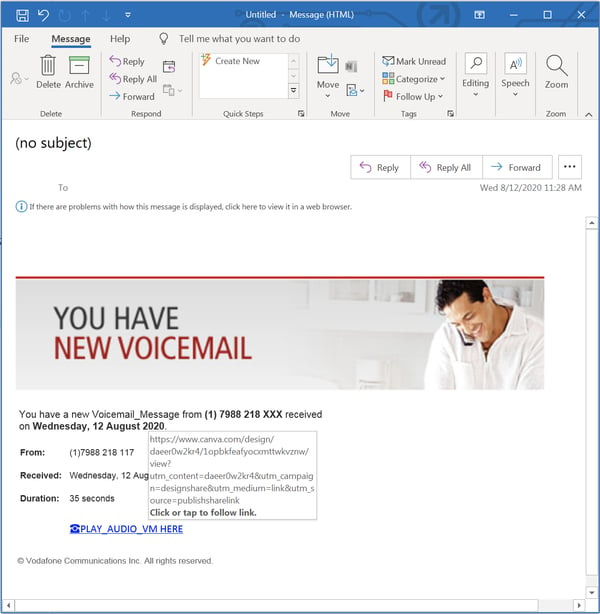
...which, so far as we know, is not offering voice mail functionality to customers.
Other common social engineering schemes include fake fax notifications:
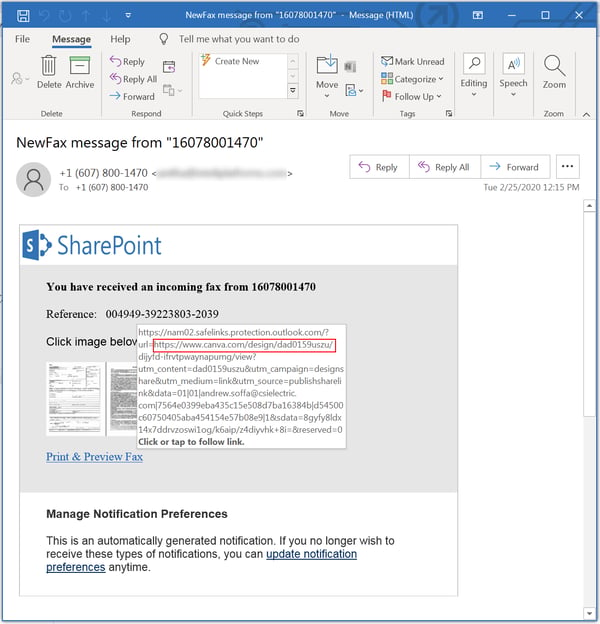
...and non-branded offers to share business documents of one sort or another:
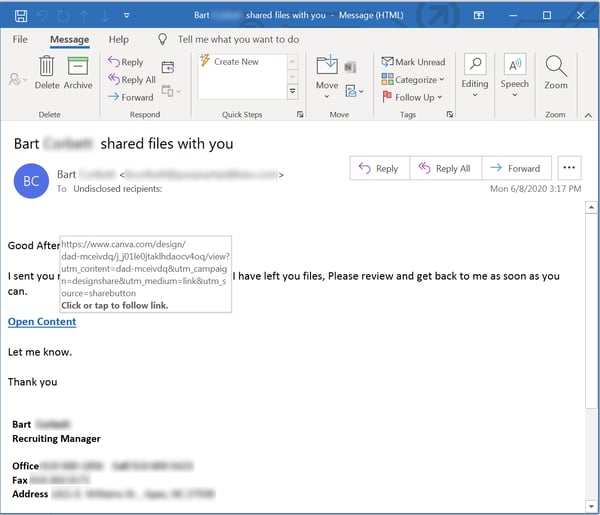
As noted earlier, the vast majority of these malicious emails lead to credentials phishes, some more credibly presented than others.
To summarize, Canva is being used to create and host files that are employed for some of the most common social engineering schemes that we see on a daily basis.
Why Canva?
None of the phishing emails we've looked at here is particularly noteworthy, save for the fact that the key document or file in the three step attack being used is hosted on Canva, an otherwise legitimate online graphic design service. Malicious actors, however, have gotten quite handy at exploiting legitimate online services and brands, so Canva is hardly alone in that regard.
Moreover, unlike other online services who are being exploited not just to host malicious content but to push out emails to potential marks (think Sendgrid and Dropbox, to name but two), Canva's unwitting role in these phishing attacks is rather more limited.
Still further, we haven't seen bad actors deliberately targeting the company to harvest credentials for accounts that can be exploited, as we regularly do with other commonly exploited services like Sendgrid, for example:
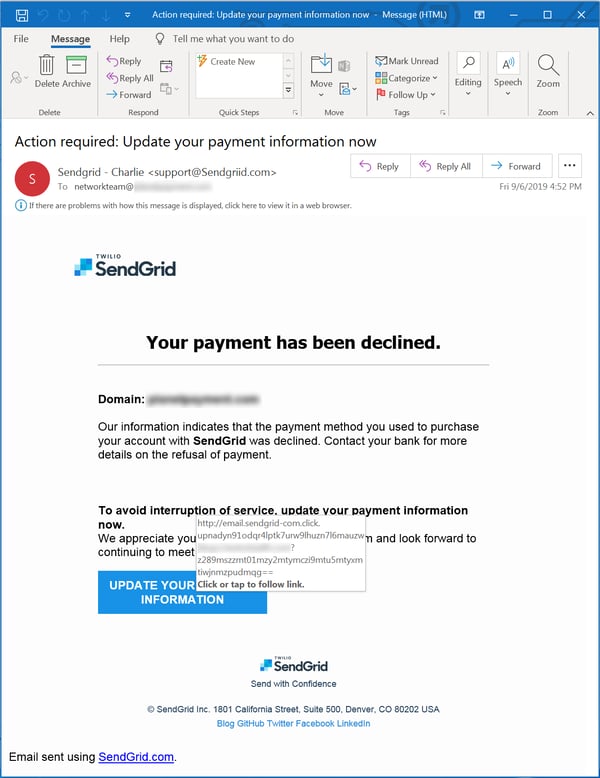
Unfortunately, though, Canva is in the unenviable position of having suffered a data breach that was discovered and reported in May of 2019. All told, the group behind this breach, GnosticPlayers, claims to have obtained data on 139 million users, including 61 million hashed and salted passwords.
Surprisingly, it appears that Canva did not immediately force users to change their passwords. Eight months later, though, in January of this year, Canva reported that it had become aware of a list of 4 million accounts being offered for sale online with decrypted passwords. Following that ominous discovery, Canva finally reset all users' passwords.
Using the Phish Alert Button (PAB), customers began reporting malicious emails with links to documents hosted on Canva accounts just one month later, in February 2020. We certainly aren't the only ones, though, to have spotted phishing emails exploiting Canva. See, for example, this write-up from Trend Micro in April of 2020.
So, did the breach suffered by Canva contribute to or enable the run of Canva-based phishing attacks we've documented here? Put simply: we don't know.
Canva does offer free accounts with decent base-level functionality. It also offers premium accounts with additional functionality for professionals and larger organizations. Free functionality of this sort is bound to attract malicious actors, and it is certainly possible that malicious actors are using free accounts, much as they did with Microsoft Sway.
It is, nonetheless, suspicious that we began seeing malicious emails leveraging Canva only after the company had reported that a list of accounts with compromised passwords was circulating online.
Conclusion
If you've been educating your users through New-school Security Awareness Training, none of what we've documented above should surprise them. That malicious actors commonly spoof trusted online brands and routinely exploit popular services such as Canva ought to be old news. But those employees do have to be trained -- and tested with quality simulated phishing emails -- on a regular basis.
If you aren't doing any of that, then a Canva-based phishing attack like the ones we've looked at here may be all malicious actors need to breach your own network and create a legal and logistical nightmare that you can ill afford in challenging economic times such as the present.















