By Eric Howes, KnowBe4 Principal Lab Researcher. For several years both Google and Yahoo have been warning users about potential attacks on their accounts by "state actors." Indeed, earlier this year Google reported that it had issued almost 40,000 such warnings over the course of 2019.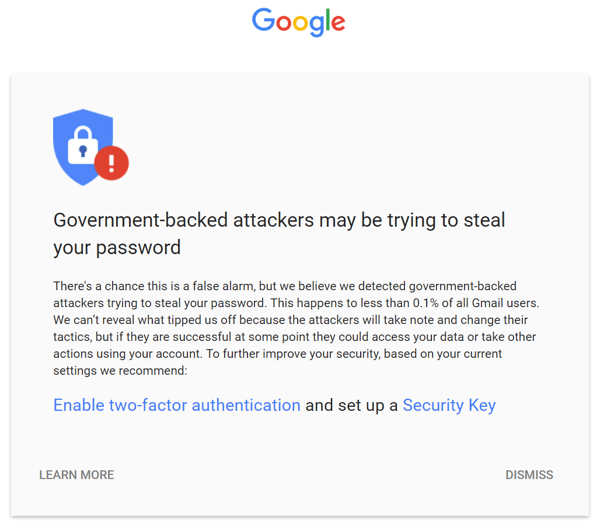
To be sure, it's an arresting notification to receive, and occasionally such warnings even make the news. And that's what makes it the perfect hook for a social engineering attack.
Malicious actors are now targeting IT admins with spoofed notifications from Google concerning alleged attacks by "state actors" on the accounts of G Suite individual users. Their goal: penetrate organizations by compromising their G Suite accounts.
Let's take a look.
The Attack
The malicious emails reported to us over the past few days by customers using the Phish Alert Button (PAB) are textbook credentials phishes that lead off with a spoofed Google security notice: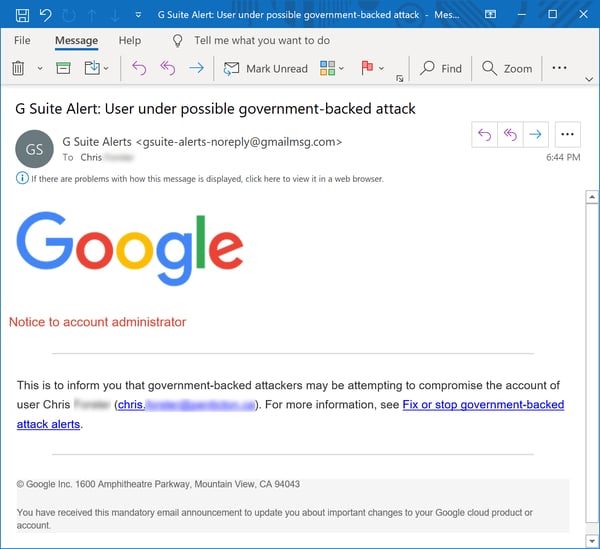
As spoofed emails go, this is a pretty good one. The visual design and use of colors and logos convincingly mimic a typical security notification from Google. The most crucial quality aspect of this malicious email, however, is its restraint and simple, straightforward directness.
For starters, this malicious spoof explicitly announces its target: "Notice to account administrator." To that end, the bogus warning itself is appropriately brief and direct -- as Google notifications tend to be -- offering specific information that is carefully qualified ("may be attempting..."), and concluding with a link offering information and guidance on addressing the threat -- precisely what G Suite admins would most want in this situation.
These characteristics alone set this email apart from most other fear-based social engineering schemes typically employed by malicious actors to motivate clicks. All too many social engineering schemes operating in this mode threaten to "jump the shark" with dire language delivered in ALL CAPS and punctuated with liberal use of exclamation points ! ! ! Not this one.
The link offering admins more information and advice takes unwitting clickers to (where else?) a credentials phish hosted on a bogus, anonymously registered Gmail-lookalike domain.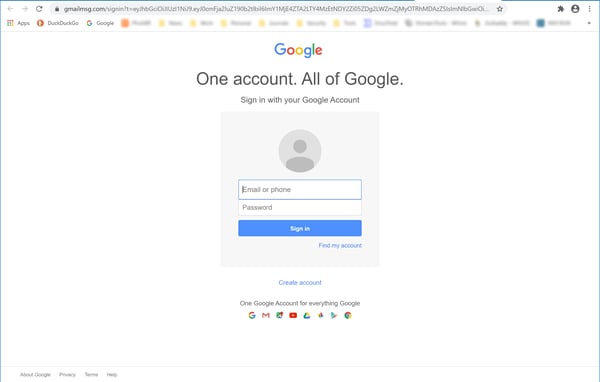
As with the initial email itself, this spoofed login page is flawlessly executed. The irony, of course, is that IT admins who fall for the ruse will actually be assisting malicious actors to compromise their own Google accounts. Indeed, one could even argue that the initial email isn't completely false. There really are malicious actors (state-based or not) attempting to compromise the G Suite account of an employee. The email simply neglects to mention that those bad actors are using this very email to do it.
While Microsoft remains king-of-the-hill in the business world with its ubiquitous Microsoft 365 productivity suite and Outlook email client, G Suite has enjoyed robust adoption rates, with Google reporting 6 million paying customers (covering tens of millions of individual seats) as of April 2020. That makes G Suite admins an attractive target for malicious actors keen on getting inside targeted organizations.
As in the recently reported case of bad actors targeting Amazon AWS admins, the bad guys may encounter problems figuring out the correct person within particular organizations to target with these kinds of malicious emails. Members of a targeted organization's IT department would, of course, be the obvious "go to" recipients of choice for this phishing attack.
Even if these malicious emails land wide of the target and end up in the inboxes of other employees, the bad guys may still end up finding their mark when worried users forward the emails to IT or the correct admin responsible for managing the organization's G Suite account.
Conclusion
If nothing else, this kind of eye-popping phishing campaign should serve as a reminder that no one in your organization is safe from phishing attacks -- even the folks whose job it is to protect the organization from attacks like this one.
That's why it is imperative to ensure that all your users and employees are stepped through New-school Security Awareness Training and regularly tested with high-quality simulated phishing emails. And we do mean everyone -- from the board room and C-Suite all the way down to lowliest cubicle-dweller.
