Let's open that doc file and watch the Matrix again.
Catalin Cimpanu at Bleepingcomputer had the scoop on this concerning news:
"Cryptojacking scripts that mine Monero via JavaScript code can also run inside Word files, security researchers have discovered.
This is possible via a new feature added to recent versions of Microsoft Word that allows users to embed Internet videos inside Word files without having to inject the actual video file inside the document itself.
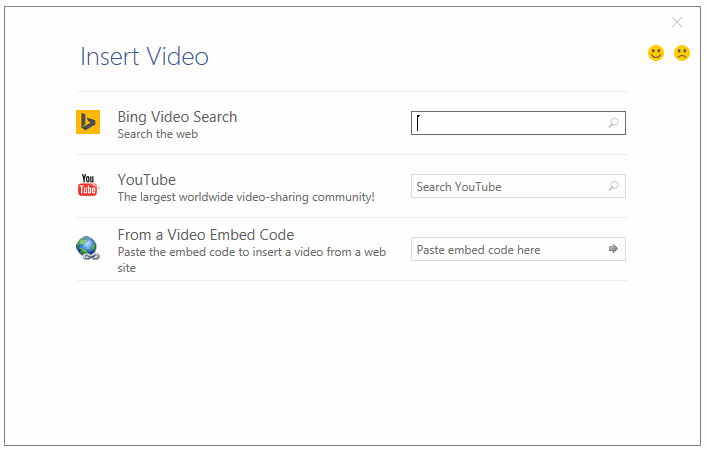
Users can copy-paste a video's iframe embed code inside a Word popup, and the video will appear in the document the next time they open it.
If they press the "Play" button that appears over the video's iframe, the video loads and plays inside a popup.
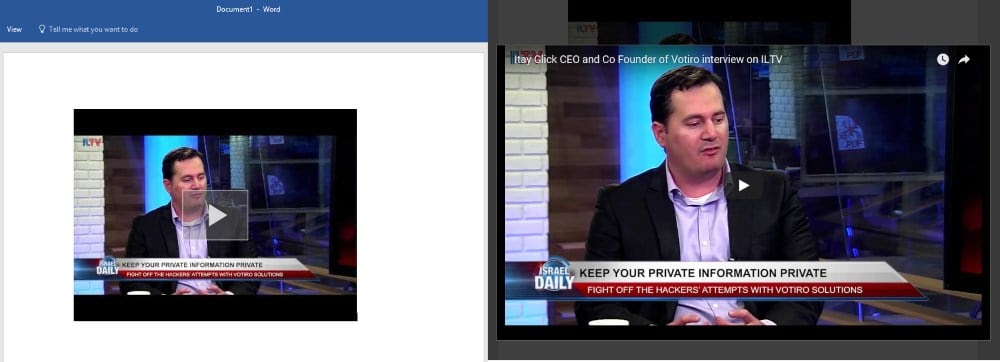
But security researchers from Israeli security firm Votiro have discovered that miscreants could leverage this video embedding system to add cryptojacking scripts with the videos, and mine Monero behind the user's back.
Word's video player is actually a browser in disguise
According to Votiro's Amit Dori, this is possible because of two reasons. The first is that Word allows the insertion of iframe embed codes from anywhere on the Internet, instead of restricting the video sources to a few whitelisted domains. Second is because the popup that plays the video is actually a headless Internet Explorer browser.
A crook can host a video on his own domain, but also make sure to load an in-browser cryptocurrency miner (cryptojacking script) alongside the video.
When users open boobytrapped Word files and play the video, the IE instance also loads the cryptojacker, which then starts to mine Monero and consume the user's CPU power. Here's proof-of-concept Word files [1, 2] that Bleeping Computer obtained from Votiro that do just that.
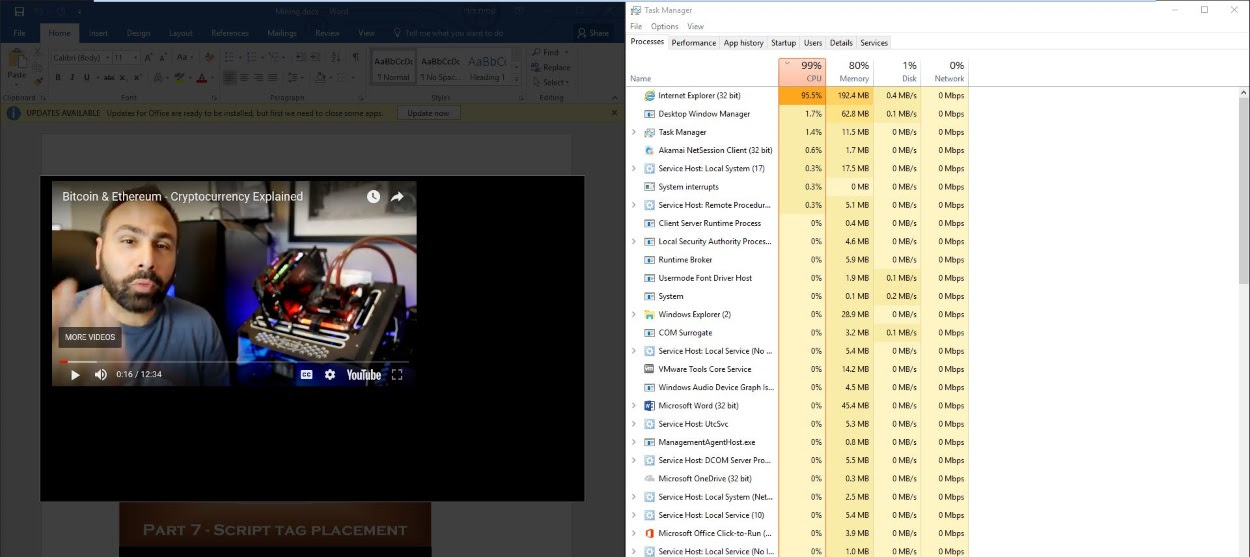
Mining Monero via Word files is probably not worth it
Mining Monero using JS-based cryptojackers because users played a video embedded in a Word file is nowhere near the ordinary person's threat model.
Any cybercriminal attempting such a cryptojacking campaign would be laughed at by all fellow crooks. This is because cryptojacking operations are only financially sustainable when the in-browser miner is allowed to run for long periods of time.
While Dori says that embedding longer videos or adding long-winding "loading" animations to the videos to prolong their play time may be a solution, an attacker would still need to convince thousands of users to open Word documents on a daily basis to make a profit.
It's probably easier for crooks to run a video streaming service or a porn site if they wanted to make money via cryptojacking. It's been proven by now that the most efficient places to run cryptojacking scripts are on sites with high user engagement rates, such as sites that stream pirated shows, adult websites, and online gaming portals [1, 2].
Mining Monero with JavaScript code inside Word files may be as dumb as hacking high-profile government sites across the globe only to make $24.
Phishing is the real threat
But Dori believes his recent findings will be abused in other ways, and not necessarily for cryptojacking.
"I haven't seen this kind of [cryptojacking] attacks in the wild," Dori told Bleeping Computer today in a private conversation. "I found this by tinkering with Word, as this is part of my job description."
Dori believes that crooks will abuse Word's video embedding system to embed phishing pages inside Word files primarily.
Crooks may limit the viewing of videos to authenticated users and may use this feature to phish credentials for various online accounts.
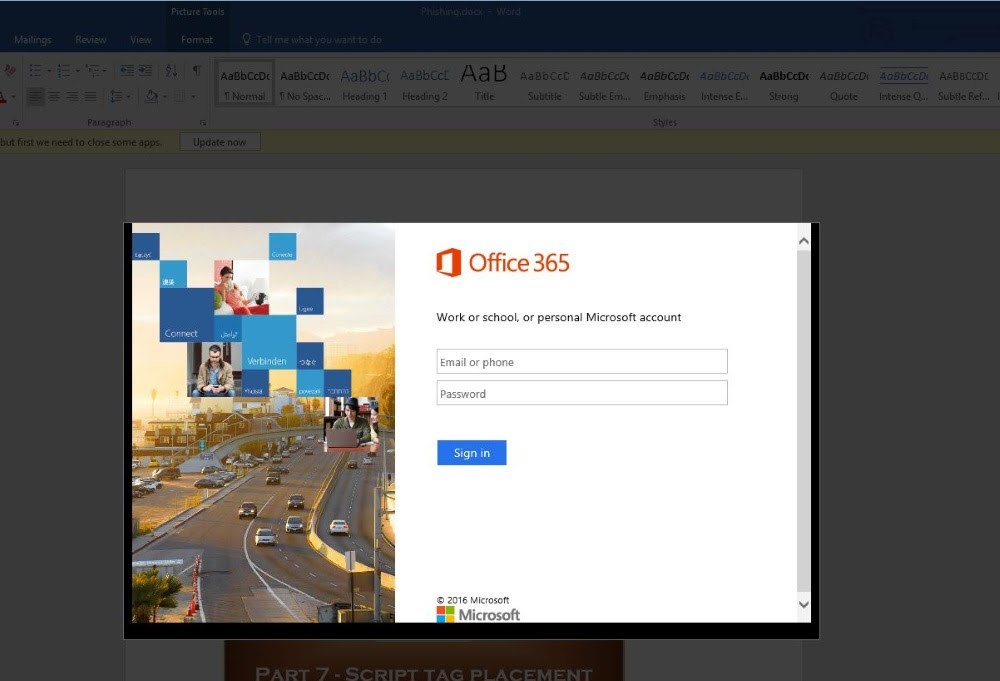
Dori also said his company notified Microsoft of the loopholes he fould, but Microsoft did not view his findings as security flaws.
In Bleeping Computer's tests, an antivirus engine caught the cryptojacking script when we tried to play the video, so at least some AV products will pick up such attacks, if someone decides to implement them in the wild.
Related: Bad News: Your Antivirus Detection Rates Have Dramatically Declined In 12 Months
The above makes a very strong case for a brand new look at your last line of defense, your users.
It makes all the sense in the world to transform them into a human firewall ASAP, and keep them on their toes with security top of mind. Step them through new-school security awareness training which combines on-demand interactive, engaging web-based training with frequent simulated phishing attacks right in their inbox. This is a very effective approach, with the best ROI of practically any IT security tool. We have just received a Forrester Total Economic Impact report that shows an ROI of less than a month.
Don't like to click on redirected buttons? Copy and paste this in your browser: https://info.knowbe4.com/training-request-a-demo
Prepare to be pleasantly surprised...
Warm regards,
Stu Sjouwerman
Founder and CEO, KnowBe4, Inc






