 As we said before, there is furious competition between cybergangs. Late February 2014 a copycat ransomware competitor to Cryptolocker was released which outdoes CryptoLocker. The malware finds text, picture, video and MS Office files and encrypts these with a strong RSA-2048 key which is practically impossible to undo. Next, it wipes out all Shadow Volume Copies. Ouch.
As we said before, there is furious competition between cybergangs. Late February 2014 a copycat ransomware competitor to Cryptolocker was released which outdoes CryptoLocker. The malware finds text, picture, video and MS Office files and encrypts these with a strong RSA-2048 key which is practically impossible to undo. Next, it wipes out all Shadow Volume Copies. Ouch.
Background
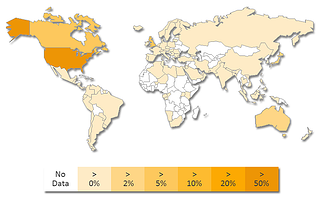
We know the cybercriminal gang behind CryptoDefense did their test-marketing in many other countries like the UK, Canada, Australia and others. They are now targeting the U.S. as you can see in this infection heatmap picture generated by Symantec. They are making tens of thousands of dollars per month with this technically sophisticated scam.
This strain does not seem to be a derivative of CryptoLocker as the code is completely different, confirming this is a competing criminal gang. Malware has bugs too, and the Symantec researchers wrote: "Due to the attackers poor implementation of the cryptographic functionality they have, quite literally, left their hostages a key to escape". But by the time you read this, the hackers said "Spasiba Symantec" ("Thank You" in Russian) and that bug has been fixed.
Infection Vector
It appears that this infection initially was installed through programs that pretend to be flash updates or video players required to view an online video, and then moved on to a variety of different phishing attacks that all show an email with a zip file and ask to "open the attached document" with is supposed to have been "scanned and sent to you".
When the hapless end-user clicks the attachment, CryptoDefense connects to four remote domains and sends basic information about the infected workstation. Then, the files on the end-user machine are encrypted, and the private key is sent back to the Control & Command server.
Ransom
If an end-user opens the infected attachment, they charge 360 Euro (U.S. $500) in bitcoin. If the four days deadline passes by, the amount goes to 720 Euro (U.S. $1,000) but the exchange rates vary wildly.
The malware makes a screenshot of the active screen of the end-user workstation and uploads this to their C&C server. That screenshot appears on the payment page where the victim can upload the Bitcoin payments. To reach this page you first need to install the Tor Browser as the payment page is only available via the Tor network, which helps the criminals hide from the law to some degree.
If the victim does not pay within a month, the private key of the encrypted files will be deleted so that access to the encrypted files is no longer possible. They are using RSA-2048 encryption using Microsoft’s own cryptographic infrastructure and Windows APIs to perform the key generation before sending it back in plain text to the attacker’s server. Getting the files back is very hard if you do not have recent backups (made without using Shadow Volume copies).
Payment Addresses
CryptoDefense allows you to pay the ransom by sending Bitcoins to an address shown in the malware's Decrypt Service page. Often people wind up paying the Bitcoins, as they find their backups could not be restored for a variety of reasons. The Bitcoin addresses used by CryptoDefense to receive payments are:
https://blockchain.info/address/19DyWHtgLgDKgEeoKjfpCJJ9WU8SQ3gr27
You can use this link to see transactions into and out of the wallet. You can typically tell which payments to this address are from ransom victims as there will be many payments with similar amounts. More at the BleepingComputer site.
Recovery
Once infected, the only way to fix this relatively fast is to make sure you have a recent backup of the files which actually can be restored. Wipe and rebuild the machine from scratch, and restore the files. We see an average of three hours of admin work for this.
Prevention
Like we said, make sure your daily backups can be restored. It is obvious that this is a social engineering play and that effective security awareness training will prevent your end-users from opening these infected attachments when they make it through the filters (which they regularly do).
UPDATE: A free CryptoDefense decryptor is available from Emsisoft.
Don't be a victim again! Get your Ransomware Hostage Rescue Manual.
 Get the most informative and complete hostage rescue manual on Ransomware. This 20-page manual is packed with actionable info that you need to prevent infections, and what to do when you are hit with malware like this. You also get a Ransomware Attack Response Checklist and Prevention Checklist. You will learn more about:
Get the most informative and complete hostage rescue manual on Ransomware. This 20-page manual is packed with actionable info that you need to prevent infections, and what to do when you are hit with malware like this. You also get a Ransomware Attack Response Checklist and Prevention Checklist. You will learn more about:
- What is Ransomware?
- Am I Infected?
- I’m Infected, Now What?
- Protecting Yourself in the Future
- Resources
Don’t be taken hostage by ransomware. Download your rescue manual now!
Or cut & paste this link in your browser: http://info.knowbe4.com/ransomware-hostage-rescue-manual-0





