|
CyberheistNews Vol 4, 05
Editor's Corner

Worst Scam Of The Week Yet: Cryptolocker
We here at KnowBe4 have been getting a lot of system admins calling us with the request for security awareness training because end users have been tricked into opening up attachments of phishing emails and infected their workstation with the cryptolocker malware. This started last September and it's not going away but actually getting worse.
This malicious hijacker code detects the personal files of a user and wraps them in strong encryption. This is both the local user Docs and remote shared folders. It encrypts every file with standard Office extensions, including images and PDFs!
The bad guys ask $300 to "give your files back". Initially they asked for just $100 but realized they were too cheap and people would pay more so they bumped up the price.
In many cases, system admins and repair professionals come to the conclusion that the only (and fastest) way to get the files back is to pay the ransom. The problem is that you could get rid of the malware itself, but the files are still encrypted, and without the malware you cannot decrypt your files anymore.
Surprisingly enough, the bad guys do indeed live up to their criminal promise (if their payment servers are up) and decrypt the files if you pay. The decryption will start at a rate of about 5GB per hour. Note that the key that "unlocks" your files is unique; you will not be able to use anyone else's key.
Malware researchers from almost all antivirus companies are furiously working on a way to prevent this from occurring, and some are able to block it from running, but these bad guys are very sophisticated; decrypting the user's "cryptolocked" files requires access to both the public and private keys used to encrypt them. Moreover, they change their malicious code all the time, and your antivirus might not catch it tomorrow. Antivirus companies are not able to decrypt the files, only the Cryptolocker malware can do the decryption. At this point in time probably the only people that know how to solve this are the NSA and they are being silent.
And how does this malware get installed on a workstation? You guessed it, users being social engineered and opening an infected email attachment. The bad guys are pulling out all the stops and use a variety of social engineering tactics, most recently it's tracking information from either DHL, UPS, FedEx and USPS, but there are many phishing attacks including banks and government.
So what does it do after a user opens the infected attachment?
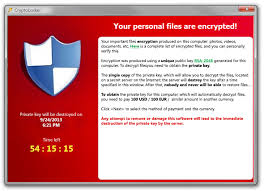 - They are presented with a cryptolocker splashscreen similar to the one to the right. - They are presented with a cryptolocker splashscreen similar to the one to the right.
- It will encrypt files on volumes (network, locally attached) where the user has modify permissions
- They are asked to pay ransom via GreenDot MoneyPaks, BitCoin, CashU, paysafecard, or Ukash of either $100 or $300 (depending on the older or newer version)
- Cryptolocker will set a timer to decrypt the files if the user decides to pay the ransom
- If the timer expires, the software uninstalls itself(!) and the data is lost
Once infected, the only way to fix this relatively fast:
Make sure you have a recent backup of the files that actually can be restored,
- wipe and rebuild the machine from scratch, and restore the files.
- We see an average of three hours of admin work for this.
Showing the need for training is that even though sometimes these attachments are blocked by existing filters as "possible malware" but users request them to be released, and the (outsourced) helpdesk released them... Users then finally admitting to opening the attachment but saying it did nothing, however they could not open their files afterward.
So, go to the KnowBe4 website and get a quote for the amount of users in your organization. Do it now, before a user gets social engineered and their files are cyptolocked.
http://info.knowbe4.com/dont-get-hit-with-cryprolocker
Win $500. Participate in the 2014 State of Security Survey
KnowBe4 and ITIC’s joint 2014 State of Security Survey is live! The survey polls organizations on their current security practices with respect to BYOD, the status of their security mechanisms (e.g. AV software, intrusion detection, firewalls and encryption) as well as the current and planned measures organizations are taking to safeguard their data and networks.
When you complete this survey, you will be able to enter our sweepstakes for a chance to win a $500 Amazon Gift Card! And there are other prizes too.
The survey should take only about 5 minutes to complete. All responses are confidential. As always, anyone who completes the survey AND leaves an essay comment with their contact information is eligible to win one of two additional prizes.
First prize for the best essay comment is a $200 Amazon gift certificate; second prize is a $100 Amazon gift certificate. To be eligible to win the prizes you must leave your email address along with your comment in the comment box of the last question. No sales people will call you and we never share your information with anyone.
Once the survey results are tabulated we will post an Executive Summary in CyberheistNews and on the ITIC Website: www.itic-corp.com. Anyone who completes the survey is eligible to receive a complimentary copy of the full Report when it’s published. All you have to do is Email:
ldidio@itic-corp.com or stus@knowbe4.com.
Here’s the link to the survey:
https://www.surveymonkey.com/s/XC6KL2J
Thanks in advance for your participation!
Quotes of the Week
"Knowledge comes by taking things apart: analysis. But wisdom comes by putting things together." - John A. Morrison
"Twenty years from now you will be more disappointed by the things that you didn’t do than by the ones you did do, so throw off the bowlines, sail away from safe harbor, catch the trade winds in your sails. Explore, Dream, Discover." - Mark Twain
Thanks for reading CyberheistNews! Please forward to your friends. But if you want to unsubscribe,
you can do that right here
|

Your End-Users Are The Weak Link In Your Network Security
 Today, your employees are exposed to Advanced Persistent Threats. Trend Micro reported that 91% of successful data breaches started with a spear phishing attack. IT Security specialists call it your 'phishing attack surface'. The more email addresses that are exposed, the bigger your attack footprint is, and the higher the risk. Today, your employees are exposed to Advanced Persistent Threats. Trend Micro reported that 91% of successful data breaches started with a spear phishing attack. IT Security specialists call it your 'phishing attack surface'. The more email addresses that are exposed, the bigger your attack footprint is, and the higher the risk.
It's often a surprise how many of your email addresses can be found by the bad guys. Find out now which of your email addresses are exposed. The Email Exposure Check (EEC) is a one-time free service. We often show surprising results. An example would be the credentials of one of your users on a crime site. Fill out the form and we will email you back with the list of exposed addresses and where we found them.
Sign Up For Your Free Email Exposure Check Now:
http://info.knowbe4.com/free-email-exposure-check-14-02-04

Funeral Notification Scam
Another one to warn your employees about. The bad guys do not hesitate to exploit the most basic fears of people; the sudden death of a loved one. The message claims to be from a funeral home and notifies the recipient about an upcoming funeral and instructs them to click a link to view their invitation and more details about the ceremony.
Of course the email is a phishing scam and clicking on the link opens a compromised website that tries to download Trojan malware to the workstation and makes it a zombie connected to a botnet. Here is a picture how this scam looks:

The example you see supposedly is from Eubank Funeral Home. This is a forgery, and the Eubank Funeral Home is warning people about the phishing attack on its website.
There are different versions all stealing the identity of different funeral homes. The subject lines, the way they look and other things are changed but they all link to compromised websites that try to download malware to the workstation. Remind your users to STOP LOOK THINK.

Do You Automate Sending SMS/Text Messages For Marketing?
My friend Chip Cooper at digicontracts sent me this, and I think it's a good heads up for all of you. There is a common misconception that text/SMS messages are subject to the same opt-out and unsubscribe requirements as with the US CAN-SPAM Act of 2003 for commercial email.
Not true.
Text/SMS messages are subject to the Telephone Consumer Protection Act of 1991 (TCPA), as enforced by the Federal Communications Commission (FCC). Prior to 10-16-13, implied consent via a pre-existing business relationship was sufficient for commercial phone calls and robo calls.
Not so now! Under new TCPA rules effective 10-16-13, "prior express written consent" is now required.
So, what does this mean to you? Just ask Guess? (the jeans manufacturer) about TCPA. Guess? is now a defendant in a class action suit alleging that Guess? violated the new TCPA rules. Plaintiffs are seeking statutory damages in the amount of $500.00 for each alleged negligent violation of the TCPA, and treble damages in the amount of $1,500.00 for each knowing or willful violation of the TCPA. For more information, Click Here:
http://www.kleinmoynihan.com/blog/guess-who-has-now-been-sued-in-a-putative-tcpa-class-action-guess/

INFOGRAPHIC: The Illusion of Personal Data Security in E-Commerce
Dashlane’s first quarterly Personal Data Security Roundup was released recently. The roundup takes a look at password policies of the top 100 e-commerce sites, and the results are staggering.
Most e-commerce sites, which often store their users’ personal info, including credit cards, have password policies that seem to be from a more naive era… perhaps one not riddled with account crackings and data breaches. Here’s an infographic of what the results of their study show. OUCH. Key findings:
- 55% still accept notoriously weak passwords such as “123456” or “password”
- 51% make no attempt to block entry after 10 incorrect password entries (including Amazon, Dell, Best Buy, Macy’s and Williams-Sonoma)
- 64% have highly questionable password practices (receiving a negative total score in the roundup)
- 61% do not provide any advice on how to create a strong password during signup, and 93% do not provide an on-screen password strength assessment
- Only 10% scored above the threshold for good password policies (i.e. 45 points or more in the roundup)
- 8 sites, including Toys “R” Us, J.Crew and 1-800-Flowers, send passwords in plain text via email
Since many of these sites do not enforce any kind of password standards, some security awareness training that educates employees how to create a strong password is not a bad idea! Here is the link to our blog with the infographic:
http://blog.knowbe4.com/bid/372245/INFOGRAPHI-C-The-Illusion-of-Personal-Data-Security-in-E-Commerce

Feb First Was National Change Your Password Day
"Cliché alert! Sometimes life imitates art and truth is stranger than (science) fiction. Peter over at Spiceworks said: "In the classic movie Spaceballs, when Lord Dark Helmet discovers King Roland's insecure password he screams, “the combination is 12345? That's the stupidest combination I've ever heard in my life! That's the kind of thing an idiot would have on his luggage!”
You would think that 25+ years later we would have learned our lesson, but unfortunately we haven’t. According to a recent study the most common computer password of 2013 was “123456”. Our old friend “12345” was the 20th most popular password, accompanied by timeless hits such as “letmein”, “iloveyou”, “qwerty”, “monkey” and “password.”
Obviously, insecure passwords open all sorts of security holes and create many (potentially very expensive) problems for an IT organization. As we approach National Change Your Password Day on February 1st, let’s review 7 tips from the Spiceworks Community (and beyond) that will help ensure a good password strategy at work and at home.
Security Best Practices for National Change Your Password Day
Enforce a strong password policy - Don’t store your passwords out in the open!
- Implement 2 factor authentication in your IT environment
- Enable 2 factor authentication on your personal accounts
- Consider using password management software
- Password protect and secure your mobile devices
- Consider a MDM solution for BYOD devices that have access to your network
Use this National Change Your Password Day as an opportunity to change some of your insecure passwords and to encourage your friends and end users to do the same. If they think that they can stick with "123456" and remain secure, gently remind them of the dozens of major security breaches that have occurred in the past year and the amount of pain they are in for if their information is compromised.
Remember, an ounce of prevention is worth a pound of cure, and you can never be too secure (there I go again with the clichés). If your users don't know where to start, send them to this how-to on how to create good passwords. Are you already following these steps both at home and at work? Do you have any additional tips or tricks to share? Had you even heard of National Change Your Password Day before?"

Major Hotel Franchise Announces Data Breach
White Lodging, a company that maintains hotel franchises under nationwide brands including Hilton, Marriott, Sheraton and Westin appears to have suffered a data breach that exposed credit and debit card information on thousands of guests throughout much of 2013, KrebsOnSecurity has learned.
If any of your employees during 2013 have stayed in Austin, Chicago, Denver, Los Angeles, Louisville or Tampa in any of these above hotels, good chance their company credit card has been compromised. I would ask for a new card just in case... More at Brian's site:
http://krebsonsecurity.com/2014/01/hotel-franchise-firm-white-lodging-investigates-breach/

Cyberheist 'FAVE' LINKS:
* This Week's Links We Like. Tips, Hints And Fun Stuff.
Super Fave. Which company used technology this year to give people a real-time Christmas surprise? I just LOVE this one!:
http://www.youtube.com/watch?v=zIEIvi2MuEk
OK, here are the Top 15 Marketing videos that went viral in 2013. Check out if you have missed any, there are a few truly -fantastic- ones like the one above:
http://blog.hubspot.com/opinion/top-15-marketing-videos
People are capable of a lot more than one would imagine. Check out this compilation of breathtaking, amazing clips:
http://www.flixxy.com/people-are-amazing.htm?utm_source=nl
Want to balance the inequities of the road-going pecking order? This is the perfect mount, Vespa's 150 TAP has an M20 light anti-armor cannon!:
http://www.gizmag.com/vespa-150-tap-cannon-scooter/30620/
Laurence Fishburne comes back as Morpheus from the Matrix movies to star in the Kia K900 Super Bowl 2014 Ad:
http://www.flixxy.com/morpheus-from-matrix-explains-luxury-in-kia-k900-super-bowl-2014-ad.htm
Everyone is probably familiar with Apple's "1984" Super Bowl ad. But have you ever seen their 1985 Super Bowl ad called 'Lemmings'?:
http://www.flixxy.com/apple-macintosh-office-super-bowl-ad-lemmings-1985.htm
Seven hi-tech firsts you may have missed at the Super Bowl. Between 3D printed cleats and game predictions determined by big data, itsa Nerd Bowl!:
http://www.networkworld.com/slideshow/138405/7-hi-tech-firsts-youll-see-at-the-super-bowl.html
Budweiser's ‘Puppy Love’ Super Bowl 2014 commercial:
http://www.flixxy.com/puppy-love-budweiser-super-bowl-2014.htm?
You may have seen Felix Baumgartner's jump from 128,1000 feet - but you have never seen it like this. Pretty incredible first person view:
http://www.flixxy.com/first-person-view-of-felix-baumgartners-space-jump.htm
Adrenaline-fueled pilots flying their Harrier, Mirage, Jaguar, F-16, A-10 Thunderbolt and KC-135 Stratotanker at very low altitude, performing fast passes:
http://www.flixxy.com/low-flying-airplanes.htm?
Harrowing mid-air rescue of unconscious skydiver:
http://holykaw.alltop.com/harrowing-mid-air-rescue-of-unconscious-skydiver-video
|

