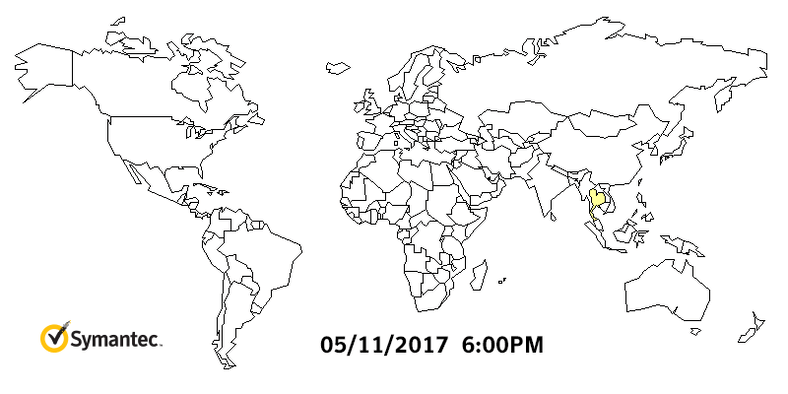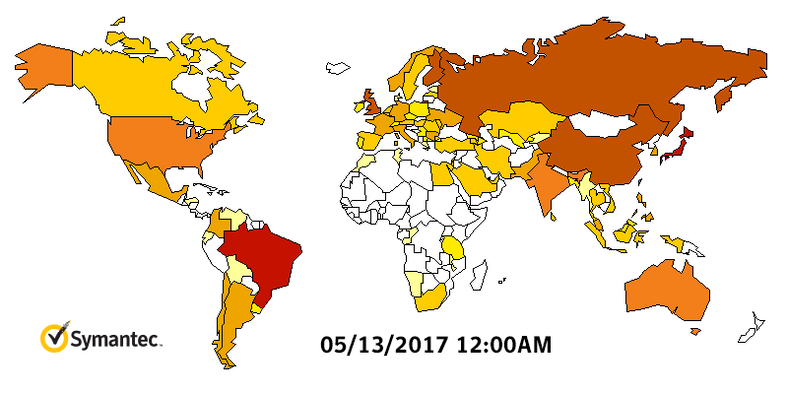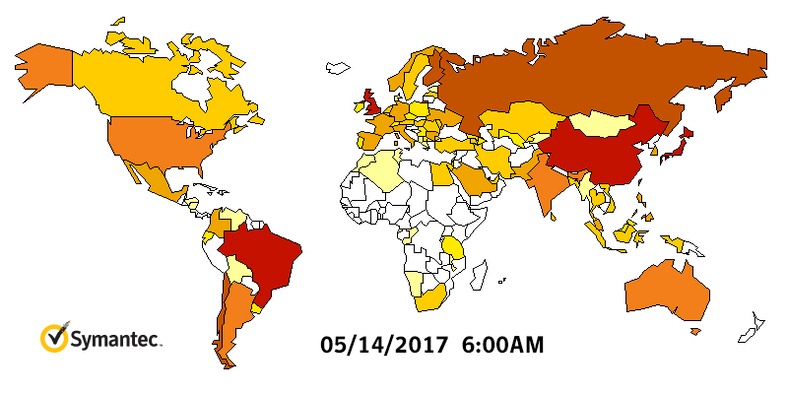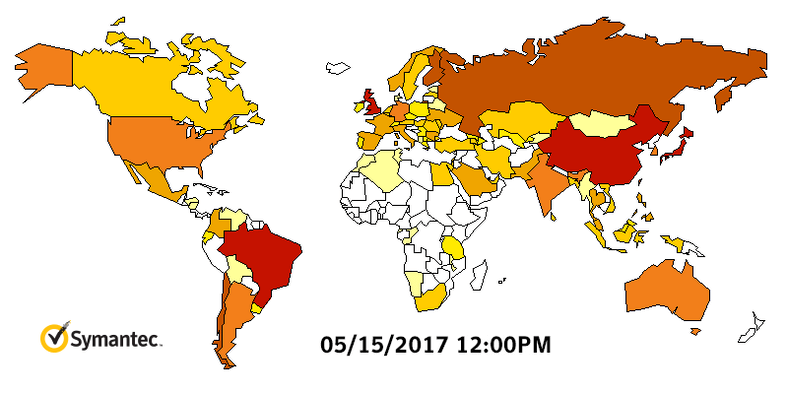
A North Korean hacking group is suspected to be behind WanaCry. Symantec and Kaspersky malware labs are investigating technical evidence that possibly suggests the North’s involvement, according to Reuters. The companies claim to have found some code in an earlier version of the WCry ransomware that had also been used in programs deployed by the Lazarus Group, which is reportedly run by the Norks. The graph by Symantec shows how fast WanaCry spread worldwide.
As tweeted by Google’s Neel Mehta, there is some shared code between known Lazarus tools and the WannaCry ransomware. Symantec has determined that this shared code is a form of SSL. This SSL implementation uses a specific sequence of 75 ciphers which to date have only been seen across Lazarus tools including Contopee and Brambul and WannaCry variants.
Remember, it's Smoke And Mirrors
WCry's developers could have deliberately added code found in Cantopee in an attempt to trick researchers into mistakenly believing Lazarus Group is behind the ransomware. Researchers at antivirus provider Kaspersky Lab said such a "false flag" is plausible but improbable. The Cantopee code snippet, the researchers explained, was removed from later versions of WCry, making it hard to spot and not a very good decoy.
Remember we’re into spy territory and the best way to approach attribution is to deal in probabilities and intelligence estimates that are never 100%, unless you can hack into the machines of the actual coders behind an attack, which is very unlikely. That said, I’d say with 70 – 80 percent certainty that WannaCry did come from the North Koreans based on the forensic evidence we’ve seen to date.
Determining where attacks like this are coming from involves a series of steps, including the process of elimination. Usually there are no victims in the country of origin. Russia was hit really hard with WannaCry, so for a change we can eliminate Russian cybercrime networks as the source. Then we look for the most likely perpetrator by checking the countries that did not have any have any attacks, which leads us to North Korea as one of the potential sources.
It’s obvious that this wasn’t one of the usual suspects since it hit worldwide instead of in a very targeted fashion. The fact that only three Bitcoin wallets were connected to WannaCry shows that it’s far from a professional organization. It shows that we are dealing with a relatively unsophisticated player who is technically astute, but who has no understanding of the commercial implications of having just three Bitcoin wallets. It shows they are in some kind of isolated ecosystem , which again points to North Korea.
Lazarus Group has been named the culprit in several other high-profile cyberattacks in recent years, including the abuse of the SWIFT financial messaging system to steal $81 million from the Bangladesh central bank, the breach of Sony Pictures, and the DarkSeoul cyber campaign that attacked South Korean TV stations and a banking institution.
"We believe Lazarus is not just 'yet another APT actor,' Kaspersky warns in its blog. "The scale of the Lazarus operations is shocking... Lazarus is operating a malware factory that produces new samples via multiple independent conveyors."
I think that the people likely responsible for this are North Koreans working out of Shenzhen in Northern China. China could easily shut this down, but they won’t.
Here is a WanaCry post that has gone viral with:
• All the updated details
• Infection maps
• How to detect it on your network
• Video with a live network infection
• Links to patches
• Technical deep-dive background
• Workarounds if you cannot patch
• Prevention Steps
• And more...
This blog post is being updated close to real-time: https://blog.knowbe4.com/ransomware-attack-uses-nsa-0-day-exploits-to-go-on-worldwide-rampage
Now is the time to innoculate your employees against ransomware attacks, as 95% of them use phishing emails as the attack vector. Get a quote for your organization and find out how affordable this is. You simply have got to start training and phishing your users ASAP. If you don't, the bad guys will, because your filters never catch all of it. Get a quote and you will be pleasantly surprised.

Don't like to click on redirected buttons? Cut & Paste this link in your browser:




