It’s an extra challenging year, harder than most, to choose the most impactful cybersecurity events. The year ended with a bang – the Solarwinds supply chain attack – which possibly impacted up to 18,000 potential victims, including almost all of the Fortune 500, involved a top-tier computer security vendor, at least a half-dozen top U.S. government agencies, and essentially brought the long feared, nation-state-sponsored, supply chain attack into reality.
The Solarwinds attack was notable for a bunch of other reasons, including that it went undetected by everyone for over half a year and that it is one of the few attacks that may have not started with a phishing attack; although we still don’t know how Solarwinds was first compromised, so who knows? Phishing attacks are involved in 70% to 90% of all malicious data breaches and it has been that way for decades.
With that said, I decided to pick out the top attacks of 2020 which involved phishing, and some of them aren’t specific attacks, but trends.
- Ransomware Gone Nuclear
For decades, ransomware attacks encrypted data and asked for money to be paid in order to free the victim’s data and computers. Starting at the end of 2019 and accelerating to over half of all ransomware attacks is ransomware on steroids. Ransomware gangs got tired of companies not paying the ransom because the victim had a good backup. The malicious gangs realized that the elevated admin access they had was the real crown jewel in what they had obtained, and that encrypting data and holding it hostage was only one thing they could do.
So, they started to search for the most important data a victim company had first. It could be personal emails, intellectual property, patents, planning documents, internal pricing schedules, employee personal logins, and customer logins…whatever was most valuable to the victim company that the company would not want the rest of the world to know about. Then they copy and exfiltrate it outside of the victim’s control. And if the victims don’t pay up, they threaten to release the data publicly, to the victim’s competitors, or to hackers. I don’t know anyone who wants their private data made public, much less given to hackers or their competitors. A good backup is not going to save you. Using this new type of threat, ransomware gangs are getting paid far more often than previously and with bigger payouts. The average ransom paid has gone from just over $10,000 to closer to $250,000 in under two years. Exfiltrated data has a lot to do with it. Most ransomware attacks start with a successful phishing attack. - COVID-19 Themed Phishes
Phishers love to follow breaking news and hot trends to get potential victims to become successfully compromised victims. For decades, phishers have used news of natural disasters, celebrity news, political angst, and anything else attention-getting as content in their phishing emails.
The global COVID-19 pandemic provided plenty of source material and topics. Global phishing went up over 6000%, most of it due to COVID-themed phishing attempts. Initial COVID-19 phishing emails focused on “heat maps” of who was and wasn’t infected, and then moved onto fake government checks when related COVID-19 financial relief bills were passed. Now, not unexpectedly, phishing is showing up purporting to offer potential victims early access to the COVID-19 vaccines. Here’s an example below.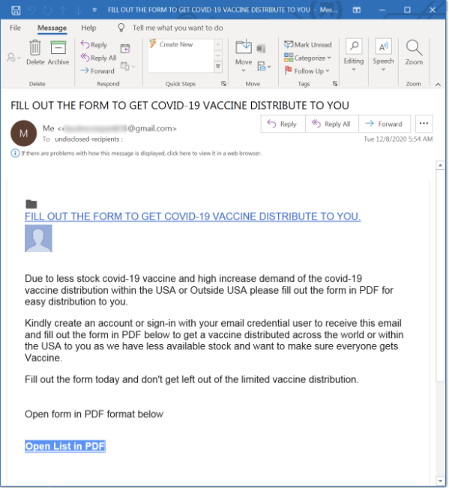
- Healthcare Targeting
Hospitals and the healthcare industry have always been targeted by hackers, but 2020 was worse than ever. Dozens of hospitals (including this Washington state system) reported being shut down by ransomware.
This year, hackers’ focused effort seemed especially egregious, especially in light of the COVID-19 pandemic. It was reported that critically ill patients were being re-routed from the closest medical facility and ended up dying due to malware attacks. Entire 911 systems were shut down.
In October, the U.S. government warned hospitals that a Russian ransomware gang was preparing to attack over 100 hospitals and other healthcare centers all at once throughout the U.S. Instead of giving healthcare workers a break so they could focus their efforts on fighting COVID and other emergencies, they must have figured that the extraordinary need for healthcare services meant the victims were more likely to pay more often and for much higher ransoms. It’s clear that not only are hospitals and clinics fair game for hackers, but they are often the preferred targets. - Twitter Bitcoin Attack
In July, verified celebrity Twitter accounts, like Elon Musk and Bill Gates, broadcasted that anyone sending them bitcoin would get their cryptocurrency offerings doubled in size. I remember seeing these offers in real-time as they happened and thinking, “Who’s going to believe this? It’s obviously compromised accounts!” Turns out dozens of individuals did take it seriously and lost over $100,000 in aggregate.
It was revealed that, not surprisingly, a phishing attack was used to compromise employees of Twitter, and that access was then used to take over the celebrity Twitter accounts. This time, the social engineering channel used was phone calls. Over 45 celebrity accounts were compromised. The attackers used Twitter’s internal management tools to do password resets, initiate new logins, and then send out the fraudulent tweets. All of this despite multifactor authentication (MFA) being enabled not only on employee accounts, but on the victim’s accounts. Just goes to show that using MFA is not a perfect security defense. In the end, three young men, in the UK and U.S., were arrested. - GoDaddy Employee Hacks
With over 20 million customers, GoDaddy has long been one of the world’s largest Internet domain registrar’s and web hosting platforms. Over the years, its employees have also been the frequent target of phishing, vishing, and hackers, usually to get control over GoDaddy’s customer accounts for all sorts of malfeasance. Once a domain is successfully under their control, hackers will often re-route emails headed to the victim’s account and/or setup fake websites. It happened at least twice this year, once in March and once in November. This is a warning that any organization’s employees may be targeted just to get access to the company’s customers. - Trickbot Takedown
Trickbot is a password-stealing trojan which targets Microsoft Windows and Linux systems. When a system is exploited by Trickbot, usually because of social engineering, it immediately goes looking for every login credential and password it can find. It will look for browser password repositories, passwords in memory, from remote desktop control programs, SSH digital certificate keys, and even steal passwords from used applications and password managers. If there is a password on your system, Trickbot is looking for it.
So, it was welcomed when we learned that Microsoft, with the cooperation of multiple government agencies, other companies, and several country’s judicial systems, was able to do a significant takedown of the Trickbot network. But within a few days, Trickbot was back, and within a few months, going nearly as strong as ever.
If you find Trickbot on your computer or network, you need to determine how long it has been active, and then change every used, stored, or cached password saved or used during the period of time that it was active. Many ransomware programs drop Trickbot as part of their initial operations. In the “old days” someone hit by ransomware might be able to change just their network logins (which ransomware used to target). Today, you must change every possible password and login digital key that could possibly be targeted by Trickbot. This means business logins, personal logins, and application passwords.
What all of these threats have in common is the hackers or malware using social engineering to gain initial root access into a device or network. Organizations must deploy their best combination of policies, technical defenses, and security awareness training to mitigate the threat. If you’re interested, we have a webinar where we cover every possible thing you can do to fight phishing and social engineering that you can fit on 100 slides in an hour.
2020 has been a bear. A vaccine is here to hopefully make COVID-19 die down in 2021. Unfortunately, don’t count on a holistic defense to defeat hackers and social engineering in 2021. The way things are looking, as evidenced above, cybersecurity events are just getting worse. Go fight the good fight!
 Here's how it works:
Here's how it works:




